Compare commits
1852 Commits
v53.0-alph
...
master
| Author | SHA1 | Date | |
|---|---|---|---|
| 7f852e94fc | |||
| 3d76c74c80 | |||
| 9bba5788aa | |||
| c25187332e | |||
| 80fa110f49 | |||
| b8f18a3d91 | |||
| eae5762d29 | |||
| c6cfa10c0b | |||
| bc6a2ba145 | |||
| f906f7f3b4 | |||
| 11582f905a | |||
| ff5c959cb9 | |||
| 23caf69614 | |||
| 6446d73cf5 | |||
| 47cbf5b974 | |||
| 9655743d8c | |||
| c2f191448c | |||
| 33a84b608c | |||
| 4a510a4b4c | |||
| e4dd5aa428 | |||
| fd72683abe | |||
| f95c6829fe | |||
| fc25163763 | |||
| 29bb5a35f0 | |||
| 96210522d8 | |||
| d94d68245f | |||
| e2681baec3 | |||
| 35e8def0b1 | |||
| 3fdcb28b8f | |||
| f54d632da5 | |||
| 6e79d1bba6 | |||
| 56f51203bf | |||
| bd2e5b8d1d | |||
| f0513b7e64 | |||
| 336300a274 | |||
| 50af4b9af4 | |||
| 3f6fcc13f0 | |||
| 1e6e211a06 | |||
| dfd5589c3d | |||
| ba173d4920 | |||
| 61a9f9d37a | |||
| 576da2e236 | |||
| f1831e947b | |||
| 915f39959c | |||
| 4d78abf2bf | |||
| 6151d664ac | |||
| 47f152ac90 | |||
| 84d515abfc | |||
| c34531b67e | |||
| 04e6e77439 | |||
| bc5add9450 | |||
| b117916207 | |||
| 2f4b93a18f | |||
| d50c772d7d | |||
| 7a1d0a92af | |||
| f2e4a79ca0 | |||
| c84c419544 | |||
| bdaa2867b9 | |||
| e2e8c4ea8f | |||
| d13f39d9f9 | |||
| ca022d8c2d | |||
| 7388485063 | |||
| 8259191167 | |||
| b99dd27de8 | |||
| 62a68f0814 | |||
| be376afc1e | |||
| f5e54b4a70 | |||
| 7135907b2f | |||
| 12ca83b550 | |||
| e4a85c30c1 | |||
| 45d23f8d75 | |||
| 40e8e1acbe | |||
| 6789dc7fef | |||
| 5eaa8196e2 | |||
| cc0f05388f | |||
| 5a366493e0 | |||
| 365e76bc9f | |||
| a93047e6c9 | |||
| 8a65c5a7ba | |||
| 60dd839081 | |||
| f4187632fa | |||
| 51f3fdbd87 | |||
| db04bc44f2 | |||
| 4e3a64b5a1 | |||
| 958acf9c2e | |||
| 95ecd3e328 | |||
| 4bc98005ec | |||
| 3f09afdee0 | |||
| 3c73bc1e56 | |||
| e38f02bc22 | |||
| 74be763f60 | |||
| 5780b6d197 | |||
| 06bfef8fd1 | |||
| d040b95ed2 | |||
| 61f01f81fd | |||
| 2b2e151f45 | |||
| ff8d63f7e4 | |||
| 848290898d | |||
| 05abe82136 | |||
| 0dba33688f | |||
| 6e53e841f7 | |||
| ecb63e82c9 | |||
| ded7c01a08 | |||
| 996881aef1 | |||
| 4b4248157a | |||
| a5e75c4bd3 | |||
| c6ab6c4b48 | |||
| ceacc9dd74 | |||
| d466cf694e | |||
| 3fcc711c5a | |||
| c21b9faefc | |||
| 1a899966a9 | |||
| 36c942e887 | |||
| 662eddbc21 | |||
| ea139e3ef8 | |||
| d6b26e7558 | |||
| 7ff46e02dd | |||
| 4ff931781a | |||
| 9aae0a62b0 | |||
| eb98f06d69 | |||
| 81561840a1 | |||
| 64bc683c3f | |||
| b4225baaf2 | |||
| e00497fd51 | |||
| d9af90d05f | |||
| 0d83307b14 | |||
| 4f3f789f28 | |||
| 6b6ed86b6c | |||
| 382b9181df | |||
| ba052105de | |||
| 4bd17611df | |||
| 41468d0d0b | |||
| a98b73c64e | |||
| 58e2618b9d | |||
| d61da93aad | |||
| 562127be87 | |||
| 917e3fe1aa | |||
| 89bee0e361 | |||
| 4c74f1bffb | |||
| 0d9de9174a | |||
| 45043537d8 | |||
| cc7ca9d0fa | |||
| 10044fcaf7 | |||
| ac0820a5dc | |||
| 83b6d64e67 | |||
| b5bf2ee017 | |||
| 09d62d2302 | |||
| 7a4676fe2d | |||
| bc2aba3829 | |||
| 926a2d4ac8 | |||
| ab7380c93b | |||
| 06b8d8bfa3 | |||
| 7016c2050d | |||
| 2787da7f90 | |||
| 7e18f8b473 | |||
| d2510b014d | |||
| 87bd8683fa | |||
| d48d3ad29a | |||
| 6675225ec4 | |||
| bb56056a68 | |||
| 93f0ff89c8 | |||
| 7811e912f4 | |||
| 238f1545f4 | |||
| c269ac9f7d | |||
| 78297132b4 | |||
| 8de87de050 | |||
| 8bc25b552d | |||
| c8c86262d7 | |||
| f836e55363 | |||
| 8cdb30cc08 | |||
| 54810e333f | |||
| 7ec13c0323 | |||
| af109d4696 | |||
| 460951df9e | |||
| 93874bda43 | |||
| 4ebabbb569 | |||
| 1f0dc1853d | |||
| 13e5fe17b1 | |||
| ec7cb6a491 | |||
| d9f49bdf1f | |||
| d5bc6715cd | |||
| 8860c90abf | |||
| 4d5abd6cc3 | |||
| de28689e76 | |||
| 5d508e4242 | |||
| 1fc43574d6 | |||
| 83602baa38 | |||
| 0634a568ef | |||
| 97322d6e8b | |||
| f7bba92c71 | |||
| fe75baa79f | |||
| 72cc4d176e | |||
| 7e1b92567c | |||
| fec5168203 | |||
| b60a888da3 | |||
| ec595c3b95 | |||
| 9d61992c8c | |||
| fd860e6c69 | |||
| d1d20b897a | |||
| cf0102f71e | |||
| 4dc5372257 | |||
| c2ddfd60bf | |||
| 47de4f520b | |||
| 27977a16ad | |||
| 4b393b9b12 | |||
| 6027aaa45d | |||
| cbfb8abf15 | |||
| 58d0161b67 | |||
| 6b351a9458 | |||
| c9e4cac618 | |||
| 34bd3c5a04 | |||
| 2f88ca2e40 | |||
| e2e7f9c647 | |||
| f8932dced1 | |||
| 17beb468f1 | |||
| bd59131d3e | |||
| 0f8217ad60 | |||
| 1515897449 | |||
| ba92918d38 | |||
| 094356e073 | |||
| 7d68a32971 | |||
| 85438d00e4 | |||
| a764149520 | |||
| 535346df87 | |||
| 412c8f9f94 | |||
| 380a88ee57 | |||
| 8404e8a59c | |||
| 6381b1aeb9 | |||
| 5cdea955e7 | |||
| b37df0bcfe | |||
| 044e3e76e8 | |||
| 1c6d633144 | |||
| 278336196c | |||
| 76c1aad4be | |||
| e5c128804c | |||
| c9956d85b1 | |||
| 524823fd05 | |||
| 283bfd744a | |||
| a1b4aa6000 | |||
| a308878b11 | |||
| 453fcd32cb | |||
| a264eebcb5 | |||
| 908638c9dc | |||
| 7e80231ac5 | |||
| 6df03e1a74 | |||
| 4b437771fa | |||
| 4043467ad9 | |||
| 5ac8fd8f70 | |||
| 2cf20c56a7 | |||
| 3b52557143 | |||
| 2a9cf32f45 | |||
| 08395de188 | |||
| 4ac17eaf78 | |||
| b5a3b54d3f | |||
| 38dc90a947 | |||
| 80f69a6f3d | |||
| 498a25c759 | |||
| 64e8dfad0a | |||
| 5ec4fef4ed | |||
| 881a2d22eb | |||
| 76c8ecd10d | |||
| 677b81765f | |||
| 9f43d48a32 | |||
| 6077d09b9f | |||
| 7144f8b7f8 | |||
| 778421cad4 | |||
| 35ccaff58e | |||
| 69132b588f | |||
| 51748ea25a | |||
| 269cf965bd | |||
| b177c73f0d | |||
| 613e55ae8c | |||
| 3697bd8d3a | |||
| 9f08c7c0f4 | |||
| 05b7d61735 | |||
| e31a6876e6 | |||
| 47be7ba42f | |||
| 033977fe10 | |||
| ab42deb541 | |||
| 8a22a90804 | |||
| c55e6dcd68 | |||
| cf379bcce0 | |||
| 2b26cd4f41 | |||
| 8bfee5b59f | |||
| 04d648d55b | |||
| 7cdc76ecf9 | |||
| aded0707a4 | |||
| 2a011f1053 | |||
| 213467d91b | |||
| da0c291127 | |||
| 27ce48f319 | |||
| 37ded2a519 | |||
| c9bdceb8d6 | |||
| 95136382e1 | |||
| 78d953bfda | |||
| 2d3d8ae5b0 | |||
| cef08b63f1 | |||
| a8e95e7310 | |||
| 5ab3c47b6b | |||
| 45c52b6620 | |||
| 93f6aea06a | |||
| 00fa8f1b50 | |||
| ac84da2af4 | |||
| f19d850845 | |||
| 7264271063 | |||
| dc63a752a5 | |||
| a70c312938 | |||
| 2ce269362e | |||
| 29ad768a22 | |||
| 679648b33e | |||
| 783786290d | |||
| e7e6cfffe8 | |||
| 08e9fb35fd | |||
| fdc9376c69 | |||
| 41c3c0ec26 | |||
| d7208ccf34 | |||
| 77410bf86d | |||
| 1d63e836ee | |||
| 668e843fce | |||
| 51e388ae86 | |||
| e7872b193b | |||
| 8d6ee7c0c7 | |||
| 7d1e244f5a | |||
| dcc736bb85 | |||
| 68568c1abf | |||
| 1b33f574bb | |||
| 568a05ad7d | |||
| c45094fdd9 | |||
| c3b7f7538c | |||
| 4b38e20f14 | |||
| d19d4ba784 | |||
| dd112a167d | |||
| 92b7fb81d0 | |||
| 404d1d466a | |||
| 06e5de4332 | |||
| eb4363dc18 | |||
| 5c93ebb54f | |||
| b8f3d93a5c | |||
| f53f01823f | |||
| 18dbb56a3d | |||
| cc8674c16d | |||
| f394fd0290 | |||
| f24899fcac | |||
| a7ba61c0d4 | |||
| babb9f3682 | |||
| b22e349d44 | |||
| bb48fe4ebe | |||
| 44a8088481 | |||
| 4c8c9bc01f | |||
| 3bb9fc713f | |||
| b761a9dd32 | |||
| 0da2ecdb4d | |||
| 31e864c16c | |||
| acc1376c37 | |||
| 939d75e5eb | |||
| 3b573bf9f0 | |||
| a231c1e90e | |||
| f229a3cb75 | |||
| 981462ee54 | |||
| d940ffb3c6 | |||
| a6d20eaf5b | |||
| b93a5e334c | |||
| c98606430c | |||
| 12c0631900 | |||
| efcceaf2c3 | |||
| 9018577a3e | |||
| 6968b9a369 | |||
| ada31d4f50 | |||
| d973e11714 | |||
| b6d7b2bff5 | |||
| 74f804a056 | |||
| f0b5e3649d | |||
| 9cc132e69d | |||
| 9419e2faab | |||
| 0566ded651 | |||
| ba9b3c217b | |||
| 79c5539edb | |||
| cfd7cd01d1 | |||
| da9f912862 | |||
| 9930cfbc07 | |||
| 7738e320d5 | |||
| 9b8735a87a | |||
| 6c10e03ce5 | |||
| 7ad3bb9e61 | |||
| 5dcf639d33 | |||
| 2da3b0192f | |||
| ada8158caf | |||
| 2071939c5e | |||
| f082278217 | |||
| abe37add6e | |||
| bc07ca94c0 | |||
| 728c962684 | |||
| ca99add006 | |||
| f771027138 | |||
| 8f1c0044b9 | |||
| 87cd828b5b | |||
| 46ccd9f654 | |||
| b1927f9de1 | |||
| b592e0e592 | |||
| 3b6cd93749 | |||
| 3a24c01f03 | |||
| b7c80841a9 | |||
| 95645f59a3 | |||
| 9138e342fd | |||
| 692ed70ea9 | |||
| 3430507ae4 | |||
| 844f3ce9c8 | |||
| 03ffb90186 | |||
| 5f9bb59b95 | |||
| 7163efdd1e | |||
| 65fb24ff1b | |||
| 612cfbf313 | |||
| 4596d721e6 | |||
| 911206eed5 | |||
| cb5cdca99d | |||
| e54ae46537 | |||
| 7c978d4e70 | |||
| d905b4387d | |||
| c31c825a74 | |||
| 6505a9fefd | |||
| de74f812ee | |||
| 82bb3f987d | |||
| a35a616de7 | |||
| ecf99bf9e7 | |||
| cfaf354fe3 | |||
| 0b51e98d91 | |||
| fa51251235 | |||
| 21fcd0bd35 | |||
| 96d558dd0c | |||
| b6e8dcab81 | |||
| fa78c53114 | |||
| 2f6b14ab6e | |||
| 2dd455ef83 | |||
| 306610da8e | |||
| 59ac1727f7 | |||
| c974b3252d | |||
| 480933484f | |||
| 0cbd8a13a3 | |||
| ae6c76fe54 | |||
| 1f098f2eaf | |||
| 11977e7017 | |||
| 27dd6aa62d | |||
| c570e4fdbd | |||
| da58f84fa6 | |||
| 755a45505f | |||
| 9d74cb9526 | |||
| 8c9d0bbe72 | |||
| 0152b38b8b | |||
| e6cf90146a | |||
| 63d1258f2e | |||
| 46bab27f94 | |||
| 2cfbba1472 | |||
| c980bda695 | |||
| feaa1c3e99 | |||
| aa1c2145bb | |||
| 335ee84540 | |||
| 5c37d50f4e | |||
| 77abf35761 | |||
| fa85c9da5b | |||
| cf53982086 | |||
| 91cbc1e09a | |||
| a7e4268d8b | |||
| 699eacf1fd | |||
| 0189438e46 | |||
| 94712f59a3 | |||
| ef93a754ce | |||
| c6ddda1aa3 | |||
| ccbca41e2d | |||
| 5b0d173078 | |||
| d6186819f4 | |||
| ea0eb85404 | |||
| 8dc43cfdc2 | |||
| f7bee988de | |||
| f2fe7f02b0 | |||
| accef19af4 | |||
| 910d7004c6 | |||
| 07cccd5386 | |||
| ac52886ea8 | |||
| c45780d79b | |||
| e14732aad3 | |||
| 26d4768447 | |||
| 9f99885272 | |||
| 0adfddd1e2 | |||
| f591a8adf8 | |||
| 0e10a820d9 | |||
| c90341dded | |||
| d5ccf4693b | |||
| e89f9a5d89 | |||
| a56ba85936 | |||
| 421f1e361c | |||
| 2391874e04 | |||
| 4779ea7850 | |||
| c367beabe3 | |||
| e1d336a178 | |||
| ee3e5f0186 | |||
| 42b7650d42 | |||
| f61d4a0d38 | |||
| 7fe9784bf8 | |||
| ed05c64482 | |||
| 16c3658040 | |||
| 515d6ff874 | |||
| fc65052286 | |||
| 6a107d4d2f | |||
| eff4b74130 | |||
| 2532ddcc18 | |||
| 44e22835c1 | |||
| 1f545312fd | |||
| 637e5964db | |||
| 26bca612d7 | |||
| 6fdda5fb62 | |||
| ed5b158777 | |||
| 4c4270f1d7 | |||
| af51631597 | |||
| ae0c980d25 | |||
| 3e4c56cf27 | |||
| 18112f9ae8 | |||
| c8eee094e0 | |||
| 78a7c194eb | |||
| f606c8b866 | |||
| 9c98972d14 | |||
| 75a03df0f7 | |||
| 76019e6fbe | |||
| 3c2bd930c3 | |||
| ed993d5502 | |||
| 22d2d702be | |||
| 8dacf6e91f | |||
| fbe1d48fe2 | |||
| 5fd7f6de7e | |||
| 592b959c24 | |||
| c6f53c8768 | |||
| 38d772e4c8 | |||
| cfce521919 | |||
| a5ab3e23d6 | |||
| b3eee6c9fd | |||
| 8d6d17d46b | |||
| 9a37e1340c | |||
| f1e0203ef4 | |||
| 726d5bde30 | |||
| f9f0fffd27 | |||
| 93840ca181 | |||
| 99aa5af356 | |||
| 0358fdac8b | |||
| 815c3026b5 | |||
| 5ed3047b7a | |||
| e16ede1cdf | |||
| 6905187b3e | |||
| 172118e61b | |||
| 8452edb94b | |||
| 0f6957bbd4 | |||
| 8c2bcc0352 | |||
| bc832575d8 | |||
| c4b7e07691 | |||
| 58fb1db838 | |||
| 2809854802 | |||
| 091a71aade | |||
| 117ab133b1 | |||
| c4a06c4689 | |||
| 0d27689c64 | |||
| 771e57480a | |||
| f8fd03482d | |||
| 10cc1224d0 | |||
| 52926cca7a | |||
| be64819ce7 | |||
| 24c228df92 | |||
| 892b3d9d69 | |||
| df21798b81 | |||
| 46d03279d3 | |||
| fe0af3bb34 | |||
| 84997386c1 | |||
| 1a389c0214 | |||
| d0060fed3c | |||
| 3d18af19e3 | |||
| b5b04454e0 | |||
| 618f7bed3f | |||
| 488a825626 | |||
| aaf6cb33d7 | |||
| 77ecef8be3 | |||
| 4be0a80720 | |||
| f573200aa8 | |||
| 48f258ff53 | |||
| b9100488cb | |||
| 9d78e050ee | |||
| b07cf1f03d | |||
| 683ef63b37 | |||
| 05580f5e99 | |||
| ecc62554e5 | |||
| f6e6de8444 | |||
| f69d92e6dd | |||
| 3edc48da56 | |||
| 868882ae33 | |||
| ff9bf76e52 | |||
| 4bc5b89cfe | |||
| bb1e5bfd54 | |||
| 27d72eda9e | |||
| 07117c65c1 | |||
| 919d4bfe96 | |||
| e38e253c25 | |||
| 14aaec71fb | |||
| c0780df24d | |||
| 0ea1605642 | |||
| bd384622db | |||
| 3366e0aa16 | |||
| dff5bb478a | |||
| d455c500a6 | |||
| b90e72370c | |||
| dd162d9f48 | |||
| d7c276b3fe | |||
| 394b691599 | |||
| ba83c555cc | |||
| b695468c7e | |||
| deae6e14f9 | |||
| 97c5378e52 | |||
| d2dd0c2ab4 | |||
| 8c7149c6a5 | |||
| d2da48c215 | |||
| 7e71b6663c | |||
| 94c83519f2 | |||
| e7d20867cb | |||
| 55ae994972 | |||
| f0945743b7 | |||
| ee35d7c70d | |||
| fe1b03bd2a | |||
| 187692af66 | |||
| b6e2a3f64f | |||
| 6f7e09ad43 | |||
| 4ddf60cf32 | |||
| 24777c9ac2 | |||
| 615ebeda2f | |||
| 4139630635 | |||
| a542701ba5 | |||
| e67a0c868d | |||
| 1afd52de6e | |||
| 64f34f1471 | |||
| 5f3e3b2691 | |||
| 1ce1f74494 | |||
| 03f558b09c | |||
| cd9fc110b0 | |||
| 7619e312de | |||
| 5d2c5de11c | |||
| e1022c2e72 | |||
| e431b324c8 | |||
| 18ad40a5c6 | |||
| 315de066ec | |||
| 85273d0f19 | |||
| ef293b57a7 | |||
| 79d316fd22 | |||
| ed60588473 | |||
| 07c128a190 | |||
| 5b1d56933b | |||
| 34cfcedc1b | |||
| f9146fdf24 | |||
| a1cdbc8324 | |||
| cd07641a9d | |||
| 9c02949e04 | |||
| 1ef62a1036 | |||
| 5672bc8cc8 | |||
| df1732745d | |||
| 30daf8640c | |||
| 4074a37e1d | |||
| 97043b0ce1 | |||
| 42ea484017 | |||
| 3f6340b69c | |||
| 884e84a4cb | |||
| 560acfc94f | |||
| fb263f5624 | |||
| 19b392b83d | |||
| 2db76c95c3 | |||
| b6fbf77dde | |||
| a4ba22e912 | |||
| 163e18ce6d | |||
| a13027905e | |||
| 8f76d9439f | |||
| f0980b5cb8 | |||
| 450c9a9e0f | |||
| 6acfdaccbd | |||
| a0e0a2a6c9 | |||
| f67e729197 | |||
| 19526b573c | |||
| b0221ec838 | |||
| a3611b7cf8 | |||
| bff1e84afa | |||
| 1d31da40ec | |||
| 0d57cfc44a | |||
| 0cfb2fb06d | |||
| d5f297ed42 | |||
| c13dbdf40d | |||
| 6173104a9e | |||
| 0c79b8b45b | |||
| 895f8d01d5 | |||
| 65dfad5c76 | |||
| fdaf22780f | |||
| 16756646bb | |||
| e4f80225d8 | |||
| 67eec9c85c | |||
| 539750d2f2 | |||
| d91226ed55 | |||
| 301fcd059d | |||
| 1cc9a08a18 | |||
| 5d1857ddd8 | |||
| 226af6f679 | |||
| 7f2c92f654 | |||
| 5b82afd5bd | |||
| d7b1877a1f | |||
| 1b6239eab8 | |||
| ad0187122d | |||
| 624e50faac | |||
| a9e9392172 | |||
| 201210111e | |||
| 53f8578749 | |||
| dc4d9e4dae | |||
| e1b0eae740 | |||
| be0ccf6460 | |||
| 7c0a327b06 | |||
| a35cba3914 | |||
| e16425310f | |||
| d503d96db0 | |||
| 335299a0cf | |||
| 7311cfdf84 | |||
| 3a9440aeea | |||
| 3210ab0ca8 | |||
| 2c734612f6 | |||
| a12dd83b1f | |||
| 44d9ceaf05 | |||
| be9d9ac9ca | |||
| 66cdb72927 | |||
| 953b96431e | |||
| 4d72ad90b0 | |||
| cccb5b10b4 | |||
| 810045eb39 | |||
| b47982bb9a | |||
| 0691b8babe | |||
| 8d1c95c650 | |||
| 19484e1a56 | |||
| 755ebf88fb | |||
| d26ea4f39e | |||
| a0f3da208f | |||
| 5166811bd5 | |||
| 86bfdd1470 | |||
| 90ef9e63eb | |||
| f2200fd442 | |||
| aff595b6ea | |||
| 6618bf5f76 | |||
| 9aa8e27ef4 | |||
| 9c782fbf57 | |||
| 931462b30b | |||
| 217553b367 | |||
| 469bbc1ab3 | |||
| 11dcc54b61 | |||
| d40d7dbabd | |||
| b80c515e88 | |||
| ed735f875c | |||
| 55b720faec | |||
| 31567c7938 | |||
| 8f939c91fe | |||
| 27bd07d496 | |||
| 42281a9e52 | |||
| 8f40c97fd1 | |||
| 9642452c48 | |||
| 8f1c3018ca | |||
| f85eb9d0c2 | |||
| 408a992893 | |||
| 23c884a5f8 | |||
| 51089fbad9 | |||
| 83b4ada670 | |||
| 7df6c676be | |||
| e338186953 | |||
| fa61a7c25b | |||
| dafd0894e6 | |||
| 06cf53d63e | |||
| fc545b4d27 | |||
| 3c5f58b812 | |||
| 7d7f580bfc | |||
| ca5d6b3317 | |||
| 9e7f9de56f | |||
| 8a204b5db0 | |||
| 690a93b71d | |||
| 0da3835a49 | |||
| a92c4086bb | |||
| 9b7771fe76 | |||
| 2265b73521 | |||
| 01aae1b346 | |||
| c2dbdcd4ec | |||
| f53b996cfa | |||
| a633622d11 | |||
| caaf76e3fb | |||
| 8811a28c56 | |||
| fdc9db9a08 | |||
| c079c3c632 | |||
| 6f76a9bfd2 | |||
| dfab1516ef | |||
| 57339d09b1 | |||
| ed23a88c08 | |||
| dae1087082 | |||
| 7a103b0c23 | |||
| 5d5a9acaa4 | |||
| 76c476ee3c | |||
| b3c6561ba8 | |||
| a4c2bb80aa | |||
| a173d30d4e | |||
| fc801db06a | |||
| 61ce537f20 | |||
| 7a766cd2a7 | |||
| 842a78692e | |||
| 540f5ce868 | |||
| be7c50c198 | |||
| 473e88c784 | |||
| da4cfce10f | |||
| 2a30436905 | |||
| 7f6d7c6a52 | |||
| 720253eca3 | |||
| 7394f2f553 | |||
| ccec62f66b | |||
| 329719fe25 | |||
| 57f4bd46e9 | |||
| 59a85bcdda | |||
| dab27cd143 | |||
| 1ff14e31c0 | |||
| c55ecbd8b2 | |||
| 99eb835e7a | |||
| 1e0b3d74f9 | |||
| 7bb0bfefe1 | |||
| f1d28f3878 | |||
| 57618a31dc | |||
| 600f9677e9 | |||
| 0d40613268 | |||
| 11f40f8a84 | |||
| c3a74a7c6e | |||
| 4dd40bddcc | |||
| 9da3cf4be8 | |||
| 50869a734f | |||
| bb788682c9 | |||
| 50afeb1861 | |||
| 0eb107abf3 | |||
| 675577fb8d | |||
| b28677a594 | |||
| 48f3dfec84 | |||
| 59930d4697 | |||
| 579aa3aa9c | |||
| ed687fc7ca | |||
| ce3d5a8cbe | |||
| 8ffbd81813 | |||
| 4119be3a86 | |||
| 8d874401fa | |||
| b4a4856223 | |||
| 8a86097997 | |||
| 7a9763d129 | |||
| a39516ff0e | |||
| 3e5e1bfdd2 | |||
| 7b667db766 | |||
| 8f1a489e36 | |||
| 6f8d0263df | |||
| 25b8b404fb | |||
| 528d0de6b4 | |||
| c9c1671e4a | |||
| 8765231de0 | |||
| e6017af4bd | |||
| 053808ba97 | |||
| 2d0182ce6e | |||
| 98f65da430 | |||
| 6a0c44d0a4 | |||
| 882d25f725 | |||
| c3210d1be9 | |||
| d4f7590c83 | |||
| d6ccf7ba64 | |||
| 0922215670 | |||
| f849e1c602 | |||
| 986c900193 | |||
| b8367959da | |||
| b05cfc32de | |||
| 358ddfdfce | |||
| 8a68fc48c5 | |||
| 87959d621c | |||
| 8b07fd57d0 | |||
| 4989928c1e | |||
| c2775a3441 | |||
| 50d31a7aa2 | |||
| 9fbe3080c5 | |||
| 8a98cd1890 | |||
| 2d62b9f729 | |||
| bb7f8df647 | |||
| 373602f0f0 | |||
| e56665ecd1 | |||
| 59d056de27 | |||
| d41372a7f0 | |||
| f62f781645 | |||
| 408d1d0e26 | |||
| d491cf1e89 | |||
| ca0f2a5a88 | |||
| fd10c35049 | |||
| 6ed3581cb0 | |||
| c2034617f0 | |||
| 6231d6ebed | |||
| 411805b05c | |||
| 8c12f4bb14 | |||
| e3349d0f07 | |||
| 92082621d6 | |||
| 54f86f4be6 | |||
| 585415b534 | |||
| 99586c4a3b | |||
| 8419b4d71b | |||
| 79e316a26f | |||
| 26a70f3cd7 | |||
| bee47f33cd | |||
| 2fcec590b4 | |||
| 3c4b312cc7 | |||
| 0354895a2e | |||
| 462db2062c | |||
| d9e24e5095 | |||
| b1aa1f5619 | |||
| a349662f69 | |||
| 28a7226235 | |||
| 97f08ad3cd | |||
| 68584a3397 | |||
| 8b4f45774a | |||
| f8428dcc0a | |||
| 6d6cd5f410 | |||
| eae8434853 | |||
| 2cff24f12e | |||
| 60be8be5ec | |||
| 981dd83c15 | |||
| 5c703f0262 | |||
| de0ebbed21 | |||
| e448015704 | |||
| d3b1ed45ad | |||
| ed140425ea | |||
| 3847f97f41 | |||
| d81e8ae583 | |||
| 7a8381d894 | |||
| 649699ad22 | |||
| 1d5289dd94 | |||
| 74c8f294d6 | |||
| a0508eccf6 | |||
| 25acd9f63e | |||
| 74a08114a8 | |||
| 71ffc661b2 | |||
| e432a22693 | |||
| f06c78f897 | |||
| 847eb80877 | |||
| ec0e58099f | |||
| e6eb473071 | |||
| f1b892bc1c | |||
| 524b5f79dc | |||
| 24f2e1d982 | |||
| c6060e5645 | |||
| d0b8a08a4b | |||
| f047fe93c0 | |||
| 6147fed61c | |||
| 54f79604da | |||
| 2f351fa5ce | |||
| 5dc3ea66cd | |||
| d9a87b3ac4 | |||
| 95b75a065d | |||
| 8c96432eb8 | |||
| 1c09ec36e3 | |||
| f1e6d164f7 | |||
| 3b90e6e592 | |||
| 45bd5ccc02 | |||
| 7bf5790f2b | |||
| 075d6fe6e4 | |||
| 4604cf0d4e | |||
| b845f8fe3a | |||
| 96063027ba | |||
| 186fb1c9be | |||
| ac4e764c37 | |||
| 5b0952f60a | |||
| 5bd5f6b28e | |||
| 55c2cacbce | |||
| 4badc42879 | |||
| 6946a01232 | |||
| da80e39064 | |||
| c1d6d81528 | |||
| d5ece0f6f4 | |||
| f6ea20a8b0 | |||
| 645492e82f | |||
| 15c68dc344 | |||
| 04b797f1aa | |||
| e60abd6c44 | |||
| d55b8176ad | |||
| 31adbba774 | |||
| 3c247a2c5b | |||
| 879f0abf28 | |||
| d97d0ec0f5 | |||
| 3916e38681 | |||
| 51ac69874b | |||
| 2d956d04f3 | |||
| 9d6bfb650c | |||
| ccdd4decf0 | |||
| f0fbfd3086 | |||
| 88b747ef36 | |||
| c6ebe36165 | |||
| 7684e83aba | |||
| 4f37975566 | |||
| 26b874bed7 | |||
| 61be5ae563 | |||
| ef1e61ebcd | |||
| 205c48d9d3 | |||
| 0e1b0a4b6e | |||
| 778dc89bb6 | |||
| 23733097a9 | |||
| 71a2d393f3 | |||
| 74ebacc0dd | |||
| 45e3b3a0e0 | |||
| 8172f730d3 | |||
| 5c85e61bb4 | |||
| 0a67cdec8b | |||
| b85668c2cd | |||
| 786839ffc1 | |||
| 8313f2e01a | |||
| 0a87c99a0e | |||
| 91fed43fc7 | |||
| 74f029566e | |||
| 571be93ae0 | |||
| 11b16c9c6d | |||
| c4ec4dbc77 | |||
| 67998eb4af | |||
| 834857b564 | |||
| 25923f1acd | |||
| 85eaba2571 | |||
| 51237f6889 | |||
| 74e753d0c5 | |||
| db56940422 | |||
| 400d764a93 | |||
| f3e2bfa76d | |||
| d4907faa8e | |||
| 62351bfbf5 | |||
| b182946ae4 | |||
| 2ae3a3e4e1 | |||
| 0ff610c056 | |||
| 661a314e28 | |||
| 106f46d053 | |||
| 643cba63cf | |||
| b5c5d8e9d1 | |||
| 36b90cd5e6 | |||
| 299a03663f | |||
| 13550d18a1 | |||
| c12eb0fdc6 | |||
| acbf881b1f | |||
| 7351e561c4 | |||
| 4e42bad6a1 | |||
| b85e748b53 | |||
| 0cc4007eda | |||
| 3003f2dd85 | |||
| ce48306a0d | |||
| 3423d39fa9 | |||
| 4834472107 | |||
| f214e4bc4e | |||
| 8fd6061bcc | |||
| 92acb6b2f7 | |||
| b6b9733afa | |||
| 89bc0bee16 | |||
| f8fc465d0a | |||
| 58fa4e9b6d | |||
| afee555045 | |||
| 5a36b4e016 | |||
| 7b3e6f5143 | |||
| 452c717502 | |||
| 661af196d9 | |||
| 39a30d710b | |||
| 8f10300c15 | |||
| 806d047729 | |||
| 0efebe3e83 | |||
| 49d9314b0a | |||
| b4b5e3a068 | |||
| 29d832e350 | |||
| 68e44285c5 | |||
| e8bfa93696 | |||
| 1abe1fd4df | |||
| 24f7847f73 | |||
| 56206f77ba | |||
| 587194ce84 | |||
| 7aac6d476a | |||
| 9e073ea5d5 | |||
| 732c438148 | |||
| 58931bc15d | |||
| 21b18cbe49 | |||
| cbcd293e68 | |||
| aacf5d4a0b | |||
| ec5fb6e3a1 | |||
| b2fc9bc266 | |||
| ca1cc2001f | |||
| f88af1dac6 | |||
| 1c6c5ea2ff | |||
| 2d316ceedd | |||
| 36c791c4bc | |||
| ee213f2bab | |||
| 01a978e33a | |||
| 6717bc0674 | |||
| 11a94c7e32 | |||
| b7c0e816a0 | |||
| 8b5547a973 | |||
| f0c29cf8a6 | |||
| e7a71143a8 | |||
| 9e342deaf2 | |||
| 109d4cf916 | |||
| c805dd8b3b | |||
| a89e8fc1e0 | |||
| f2065a463c | |||
| 299489c701 | |||
| 50a578c32a | |||
| 7d417da5fd | |||
| e6a13e5a93 | |||
| 9a46fafb53 | |||
| 6fb2f25e65 | |||
| 9e67f982ab | |||
| 5b6ed92da4 | |||
| 2969c6660f | |||
| 776e32c27f | |||
| 9e1c368cd9 | |||
| 572d16d5a5 | |||
| 29e2461cd1 | |||
| f39112f914 | |||
| 0145ccfec3 | |||
| c2c8e6227c | |||
| ab404680df | |||
| cfa2da8fea | |||
| b3b3ae4660 | |||
| c4d131aaf9 | |||
| 9c975b318a | |||
| a1638868ea | |||
| 3806ccc68c | |||
| 06b69bb95a | |||
| d8bfdaa058 | |||
| 03efb99754 | |||
| b390d9787b | |||
| 2e908f38d2 | |||
| f973422581 | |||
| 5bcbe56f4b | |||
| 833f816b99 | |||
| 5ccea3262f | |||
| 9611eac1cf | |||
| 43119694fb | |||
| cbea3adc7e | |||
| 4813aa549b | |||
| 96706cf11e | |||
| a81d013e45 | |||
| 857cbd8c24 | |||
| c9543519c7 | |||
| d34894e965 | |||
| 70abeda9d4 | |||
| dceef9d1db | |||
| 9386fb5581 | |||
| 56acb4cff5 | |||
| 1eac4185d2 | |||
| 05021ac62e | |||
| a2b5e1e7cf | |||
| d9a1c83300 | |||
| a4a9b9a675 | |||
| c61e633236 | |||
| 8783ae9ce8 | |||
| 3264fbd9c3 | |||
| b8b3a4f7ed | |||
| 7f1f9e124b | |||
| 9b1cf28e89 | |||
| acc5a1c2df | |||
| 9a4032f4cd | |||
| f113cf84c3 | |||
| c92ece7960 | |||
| 3e5667fb34 | |||
| 2bf238f384 | |||
| 3edf7af85e | |||
| 4b8b2d81a0 | |||
| fde8035332 | |||
| 01bd2a4f6d | |||
| 6d4b49d061 | |||
| 8e60f412e4 | |||
| f60a87f97f | |||
| 449e32a8ca | |||
| 35a9d3d1e1 | |||
| c66d1b08e7 | |||
| 0a63b6545d | |||
| a8051b88e4 | |||
| 87ce12925d | |||
| d6a7531c67 | |||
| 3a77e18ae8 | |||
| a635ae5dfb | |||
| 02bac31e6a | |||
| e5d23f6b40 | |||
| 5fc48a1027 | |||
| de7a8650f7 | |||
| 9c7170fc26 | |||
| 9406f32194 | |||
| 33759ab604 | |||
| f97c9a05a9 | |||
| 94abd71787 | |||
| 45f1dfa912 | |||
| d6280d2d7a | |||
| 67360332ab | |||
| b880c9da61 | |||
| 1b0c9f66d9 | |||
| 7eda26a1d0 | |||
| b89e247263 | |||
| 35fd4e343c | |||
| 47cf0e1640 | |||
| 5e7258ba2d | |||
| 6e6a993494 | |||
| 772fa4e06e | |||
| 78dc31f6d6 | |||
| 459396ed5b | |||
| 88b08c79cd | |||
| cf269c982b | |||
| 36c11cb5d4 | |||
| 517b8665c0 | |||
| 149aab6b1e | |||
| c5a1a038d2 | |||
| cd322f39a4 | |||
| 8f2b674910 | |||
| 7d65d8c173 | |||
| 8b6eec2b46 | |||
| 13164a2d0d | |||
| c4a1583e99 | |||
| d10c8598f7 | |||
| 40db113d07 | |||
| 041e14a4d5 | |||
| e67fdc2ce4 | |||
| 75534b4e6c | |||
| 94c0665343 | |||
| 71adc43d17 | |||
| 94f86465e6 | |||
| bb4bf835b0 | |||
| b4f1b4dbbf | |||
| f90c17f748 | |||
| fdac8fba6a | |||
| d055560f6f | |||
| 27f87240ec | |||
| 17d83c1a1a | |||
| 8fa3a9db6b | |||
| b0fb59f735 | |||
| 64d08dd6bc | |||
| 824dec4f9e | |||
| 3d2b0703be | |||
| e25137ce94 | |||
| 6ee25c2bf5 | |||
| 6309822d33 | |||
| d04ff8457e | |||
| c6e3c013e0 | |||
| e373a0f6e1 | |||
| acce871308 | |||
| 61e706641e | |||
| 1e5e2ca418 | |||
| c62bff5c70 | |||
| 3bae3ed5ba | |||
| aa91ea1680 | |||
| d244198438 | |||
| 871e7ed87b | |||
| 48901d156a | |||
| 8b4e6c95aa | |||
| fd1aa74ff3 | |||
| b3e92ab7cc | |||
| 30fbaba4df | |||
| 72e1858926 | |||
| 3ad6ed465e | |||
| 3fcad90996 | |||
| 383b8ca943 | |||
| 6a98aa7ba0 | |||
| 2037449fbd | |||
| e18bd0f32c | |||
| 715fff06cf | |||
| 3675a68009 | |||
| 062dd6c023 | |||
| bc17b4e450 | |||
| 682e12fe57 | |||
| 6cb27ca78c | |||
| c38ae56232 | |||
| 04f1449003 | |||
| 53a69ff5bc | |||
| e8c02278eb | |||
| 457611f079 | |||
| 09aca71822 | |||
| f90193ab76 | |||
| ffced9b4c0 | |||
| 0b3395b520 | |||
| d4a20165ef | |||
| 089f0826cf | |||
| b83d53e681 | |||
| 14456b5a29 | |||
| 517e40703f | |||
| 7f7282a975 | |||
| 6fd415eab2 | |||
| d4083e6a3e | |||
| 3192027f52 | |||
| 2a402310cc | |||
| 1469e13df8 | |||
| 92585ecd93 | |||
| 205d64ab29 | |||
| 3812aed9e9 | |||
| a83f5a0f5f | |||
| 19c40eeb18 | |||
| 61d2b46a02 | |||
| b93c7e026c | |||
| ec687cad75 | |||
| 6b691ae7e3 | |||
| 40da3653d3 | |||
| 77a5894fa0 | |||
| 11bcf46063 | |||
| 2dd2f5febe | |||
| 2de13258ff | |||
| 40391a26a2 | |||
| 50186412e4 | |||
| 9892c3cbb7 | |||
| 887e93a4f2 | |||
| 7f1a82365c | |||
| 8996071cd0 | |||
| cc166b8091 | |||
| 0260176fef | |||
| 09e2b181e4 | |||
| 4dafbb89df | |||
| 5e08ad8c60 | |||
| 6366ab8afc | |||
| 2980073bca | |||
| e8b9f72885 | |||
| b502317caf | |||
| 5385b8c4ab | |||
| 17fe261170 | |||
| 3d5276484a | |||
| 542b814814 | |||
| 0473c73860 | |||
| a6fd4d1db1 | |||
| 95251e98da | |||
| 08a5410b88 | |||
| 93a8f89191 | |||
| 4fdf322193 | |||
| ca11a88189 | |||
| a290b3ad3d | |||
| d924c01518 | |||
| 1738f9efb1 | |||
| 3ef5ba3ac7 | |||
| 2969ab5b13 | |||
| 3405bae6d8 | |||
| a4eaf9494e | |||
| ea6e9be787 | |||
| 0ebe5d0fa8 | |||
| ff77f7260c | |||
| 93c3457d18 | |||
| bc371c8c9d | |||
| 622b70aa37 | |||
| c83670f708 | |||
| c399bb1d2d | |||
| 0a11a87fd0 | |||
| 91521dbc84 | |||
| 14c1620994 | |||
| 0da73d606b | |||
| 6a0f162d64 | |||
| 038201fb07 | |||
| 91c8da5f12 | |||
| 22198d420a | |||
| 6becf50fe6 | |||
| 4fb3040042 | |||
| 5005376742 | |||
| 48f95f2ac7 | |||
| e5c14eb700 | |||
| 7a3810f6ca | |||
| c8d7694fd3 | |||
| 343f77c5e9 | |||
| a0ec17955d | |||
| e195aceb54 | |||
| 6882a64bf2 | |||
| 806d6edc6d | |||
| d1ab8fd10c | |||
| db97478cd1 | |||
| 48ec3da18d | |||
| 8c35bf5d11 | |||
| a3bffb83bd | |||
| b30b988137 | |||
| f820ecbacb | |||
| 3acef78f59 | |||
| ac16b9c77b | |||
| 1069915372 | |||
| 978e51b515 | |||
| c5374b60d8 | |||
| 2a2b80902a | |||
| d82791a933 | |||
| d89e9834ff | |||
| 04c7ed94da | |||
| c82d6f70fe | |||
| dd29583735 | |||
| e3ad7055dd | |||
| c1c368bce9 | |||
| 73f03c449f | |||
| 31ec621d3f | |||
| 8f02a5bc40 | |||
| 73811e49be | |||
| d7ab2f83e4 | |||
| c0f9e6ab2b | |||
| 7cd2c650cb | |||
| a1f10513ea | |||
| 74f18db85a | |||
| 2ad3fbdbd3 | |||
| 68a44bcbb4 | |||
| 1f15e287fb | |||
| 65b64f44b6 | |||
| 643206a3da | |||
| 05ac6dd0ec | |||
| daff5f6fa6 | |||
| 018fb2a321 | |||
| 4f22afac7f | |||
| 94bbb6bab4 | |||
| b9266bba1d | |||
| 68efac4cc8 | |||
| db5706d949 | |||
| 3ffdd67904 | |||
| 83de87b18d | |||
| 99016960fa | |||
| 52efb2af7a | |||
| dbe0056c95 | |||
| 987c996cce | |||
| a1cae1ae74 | |||
| 0938d7bab2 | |||
| 490d81657f | |||
| 4170529e39 | |||
| ffae671b27 | |||
| 48861e57e1 | |||
| b74b79f11c | |||
| 13534e33bc | |||
| 148daa94cf | |||
| 88b08d4ac5 | |||
| ea76ea91af | |||
| 8af0d4fa7a | |||
| 877d6a5af2 | |||
| e0cd64391c | |||
| 464ffcd7e6 | |||
| 16e8d6ca7a | |||
| 21b21d2adb | |||
| 6973bb459c | |||
| 1571e067e7 | |||
| 1789fd902b | |||
| 8f4ab83301 | |||
| eeef37154d | |||
| be563241d6 | |||
| 002780df8c | |||
| 901670fffc | |||
| 3a403cd120 | |||
| 25321e7262 | |||
| ca947c6ae4 | |||
| c9f62822a6 | |||
| 240bcbfbee | |||
| 1262edee61 | |||
| 2f5ae9b294 | |||
| fbd9f344af | |||
| 323da46204 | |||
| 28f06b41e3 | |||
| 77ca6af2d9 | |||
| e663b8a968 | |||
| f8ec9cebdd | |||
| 24df3274f1 | |||
| f5a4ec0cbd | |||
| abbbf8ef0e | |||
| b9c8329778 | |||
| 8f68ee3e9e | |||
| 4d2c26790f | |||
| ab492c58c3 | |||
| 4fc7490405 | |||
| 11b0b779b8 | |||
| 4ae5967e09 | |||
| ebd233bf6e | |||
| f2ed64c576 | |||
| f09c860d96 | |||
| 753c4695a6 | |||
| 7655648174 | |||
| f8472fe501 | |||
| d82475a7c3 | |||
| 008257283b | |||
| d9e935de3c | |||
| e73eeefa64 | |||
| 744944a9ab | |||
| 5631fadd4a | |||
| ea54827582 | |||
| 28ba2a705a | |||
| a9def5992f | |||
| 9aa9752dc4 | |||
| eb2a9b2493 | |||
| 60cfacadb3 | |||
| 85e633dc60 | |||
| 61aeaa4714 | |||
| b802ecb18f | |||
| 9b5d4521d1 | |||
| 8f34f8e0ff | |||
| f683383ba3 | |||
| 83aa56e353 | |||
| 467b3d8602 | |||
| 183a62448f | |||
| ac751a74f2 | |||
| 457ef9ec2f | |||
| a6c93b3982 | |||
| ccaf06973b | |||
| ce3c077d06 | |||
| edec5cc366 | |||
| 8a99bb350c | |||
| fc47792df2 | |||
| e5d00be8f0 | |||
| ac7ad78d1d | |||
| cf6f614f5b | |||
| 00e17281dc | |||
| 9a4982ec0e | |||
| 0a97660506 | |||
| 3737b65f53 | |||
| 635cacfe54 | |||
| a126a32109 | |||
| c9e7f1ccfa | |||
| ff9370b714 | |||
| b1fd2ba48b | |||
| bdf69cd198 | |||
| 22695f464b | |||
| 44e129ea3d | |||
| 6ff3d1eb36 | |||
| a389572243 | |||
| 51d98fac09 | |||
| d71321027b | |||
| ed4c9202b9 | |||
| 5b931b06e8 | |||
| d3eda589bb | |||
| 0be33e2408 | |||
| eba3470a81 | |||
| 1c997693ff | |||
| 76b24fa6aa | |||
| 3b95e04b56 | |||
| 3ec7dae496 | |||
| a269e53f88 | |||
| 1789fea4f1 | |||
| 679ca59233 | |||
| 82d20c328d | |||
| 41a55ad5f2 | |||
| 2c1e4ae542 | |||
| 910d4e2e59 | |||
| 2bf9e6a773 | |||
| d279839ba6 | |||
| 98bb8ad203 | |||
| a281090cdc | |||
| 44316934f3 | |||
| 18048832da | |||
| 497f6ed58c | |||
| 63b924f101 | |||
| e1e40847e0 | |||
| 5743fe303c | |||
| 89e0aed652 | |||
| 59ae0b1028 | |||
| 69c278c3ba | |||
| 4290b4e882 | |||
| efcaa3de8a | |||
| cdeb0abe79 | |||
| 450adab519 | |||
| 500c129d48 | |||
| 7ae034a23c | |||
| 754ec610d1 | |||
| fe752c8be3 | |||
| da3ba2a97f | |||
| 22e51e2a08 | |||
| c6d55296fb | |||
| f89bb3f1c2 | |||
| 64a6eb794a | |||
| fe46ea79ce | |||
| d256908a5f | |||
| dedfbf04b6 | |||
| e080becba5 | |||
| 76bc2bce25 | |||
| 7f4a671b09 | |||
| b373fe2a58 | |||
| 95f1d6ecf6 | |||
| 3028a7a61a | |||
| 06d9d61558 | |||
| 1dd683c81f | |||
| 2c56d90a6f | |||
| df01fb87ce | |||
| ce66da10a4 | |||
| e1034faf1f | |||
| d4cfd1e885 | |||
| 6cdfd1a443 | |||
| ca16792723 | |||
| 6e2479dc0f | |||
| bbb29237cc | |||
| fec0c99287 | |||
| 258e8ff805 | |||
| a74170e2b0 | |||
| e29a301578 | |||
| 1031312f82 | |||
| ddfdf7cb47 | |||
| 649e49e0fa | |||
| 908a8d66f4 | |||
| 4a91b866a4 | |||
| 0912b03f62 | |||
| 12f80bdf65 | |||
| 88216743a5 | |||
| fa94f9b3c1 | |||
| 620a0ee29c | |||
| a25df4c942 | |||
| 7fa0025baf | |||
| 80ac9dfa1f | |||
| a93ce5d9f1 | |||
| 367972155a | |||
| 985c164cd0 | |||
| f5ffeff971 | |||
| 31e7c72f64 | |||
| 2f6deda172 | |||
| 39594629e5 | |||
| ca30ba4994 | |||
| 5338b6fb60 | |||
| bdf0e5ed56 | |||
| 89474d014f | |||
| c84a59fd95 | |||
| 598ee751f5 | |||
| 2e4e0a6327 | |||
| 4d35be7ccb | |||
| f3bd095fe9 | |||
| e794611920 | |||
| f450c2172b | |||
| 6a7dac32cc | |||
| 6900924aa6 | |||
| 7c2be97879 | |||
| 5e414ff5cb | |||
| 13aa4a0290 | |||
| 76672ed767 | |||
| a5ae7d17a3 | |||
| 54b64e3f3c | |||
| 17ba1401cf | |||
| e09e5ab8db | |||
| caed9d833c | |||
| d9f76d3add | |||
| bb2325cad2 | |||
| 9a0edfe887 | |||
| 0277ba8102 | |||
| b907dd7e83 | |||
| 83bb51b988 | |||
| f3c87367fb | |||
| ffc8280c0c | |||
| 346b945ee3 | |||
| b86f625b02 | |||
| 431b55f47f | |||
| 4120419cd5 | |||
| 9f30adee64 | |||
| a19a3d2a35 | |||
| b6533689cf | |||
| ae83b83590 | |||
| 4977d01fec | |||
| eab3a0b714 | |||
| dd25413c98 | |||
| 3d109664bb | |||
| 595eaf540c | |||
| 31b1f6624e | |||
| e95d2afc95 | |||
| 996e760f8c | |||
| 6c2f3ad33a | |||
| f7dea0a1e9 | |||
| 911a98c675 | |||
| cda46d8342 | |||
| 2182bdfbe8 | |||
| 21b5c5dea7 | |||
| b527e5c65e | |||
| 1755543594 | |||
| cf2a6fd554 | |||
| bc58c10f34 | |||
| 3e3acd5897 | |||
| 6be84b8516 | |||
| 7a05580c62 | |||
| 48511d1f9b | |||
| 69449f8593 | |||
| 09ccb74d69 | |||
| ebcf5bec9e | |||
| 3970c1db9e | |||
| 0861490d39 | |||
| 80c95cbac4 | |||
| f18197c22e | |||
| 98698c8e68 | |||
| ea713abfc6 | |||
| eb532d61be | |||
| 29ce831774 | |||
| c7cd524f21 | |||
| 8538685685 | |||
| 9e573ea97f | |||
| f8cdfbcd93 | |||
| 0e2e54238c | |||
| ed2f829af9 | |||
| 7e92f86244 | |||
| 66cf6b7641 | |||
| dcf4ebfbad | |||
| b24539cc25 | |||
| f52cb0e334 | |||
| 4d0c29672b | |||
| a6fe71d24a | |||
| fa778f2a87 | |||
| 12e25652e6 | |||
| cb5593f09e | |||
| 63ed779776 | |||
| 998069f440 | |||
| 63ba049ccb | |||
| 8081967187 | |||
| f00cc290b4 | |||
| 8c3cb3a834 | |||
| 4397bc9137 | |||
| 71fd837308 | |||
| bb07b0e78c | |||
| 8d7fceb6da | |||
| aeb7846200 | |||
| 4fac8f71c4 | |||
| e4002913d9 | |||
| 9499122d96 | |||
| 656b755a34 | |||
| 0bf6323e6f | |||
| dc955fb846 | |||
| 0eb7a927e6 | |||
| 989a5816b1 | |||
| 049841acb1 | |||
| 16499e9611 | |||
| 4e36051192 | |||
| bcf38ca80b | |||
| 71c81992f5 | |||
| b6567f3de9 | |||
| 3cdc4a93d7 | |||
| 34d0054d95 | |||
| 7d89436f27 | |||
| 54cf998f78 | |||
| 35fd208af9 | |||
| 40a62aa38d | |||
| 1ed4c45051 | |||
| 4a0074d1ab | |||
| 132e0fa503 | |||
| c864c8ebb0 | |||
| 063b731054 | |||
| d7c282c0fa | |||
| b24dd123d0 | |||
| 8b0bc463c5 | |||
| 4d31983e06 | |||
| e018583082 | |||
| 6348826519 | |||
| b55a986d52 | |||
| ba78702686 | |||
| 32327e15c1 | |||
| d1306aee26 | |||
| ac77e65d82 | |||
| 6b7032ccaf | |||
| 6ef86fbde6 | |||
| 0176d8676c | |||
| da1b9054ad | |||
| fba479944d | |||
| 791b4114c6 | |||
| 8cdc6e766c | |||
| 319db71e82 | |||
| 907e0aaa24 | |||
| 5e0f37c925 | |||
| 06018367a1 | |||
| 7b2d67976c | |||
| 7a0fbb6a31 | |||
| 1f18162d56 | |||
| eba592c7e5 | |||
| 46bfeca8c2 | |||
| eeedf0db72 | |||
| 1ad970741c | |||
| f61c951ca0 | |||
| b9e321c45a | |||
| 8a9a4fe427 | |||
| 44c4a62820 | |||
| ab7dfb7f43 | |||
| 3c7789defc | |||
| 82432a3d40 | |||
| 75f6bc8b5d | |||
| b53b4832d4 | |||
| 9719fc319d | |||
| 9340f8ba04 | |||
| dd01dd54c6 | |||
| 1a04c1314e | |||
| ec03969d98 | |||
| 1621cd5e48 | |||
| 0006ee04b4 | |||
| 08fbc37870 | |||
| 9859cc8889 | |||
| a4be5471f1 | |||
| d1e02e407b | |||
| ed9bc336fa | |||
| f84f9b7c44 | |||
| f74b327403 | |||
| e4a8dcf0dc | |||
| 9eee26bc35 | |||
| 76293cab6a | |||
| 4a0ff9ea33 | |||
| 8b2b0898c0 | |||
| 956c94f812 | |||
| 2336d0a20b | |||
| a4a0ec5cee | |||
| 8abe26083c | |||
| c4bba2258e | |||
| f84e051b50 | |||
| caa1d2c22e | |||
| b72c6f57c0 | |||
| 7c87abbe78 | |||
| e6628e56df | |||
| c7b34d3b26 | |||
| 147e02379a | |||
| 05bbd88f95 | |||
| e080614c30 | |||
| a0aca310e9 | |||
| b5c072dc18 | |||
| 31d3aec893 | |||
| 1c82abf074 | |||
| 1c5988c770 | |||
| b8a6f2a7ad | |||
| ec9f9fcea8 | |||
| 7fcb3ce836 | |||
| 8f5305f383 | |||
| 9d6da7199d | |||
| 83cf157178 | |||
| 21f5333723 | |||
| d5c92cd548 | |||
| ce90d07e0e | |||
| 903ba2d2b4 | |||
| 64351a0c19 | |||
| 0d09e9c9b5 | |||
| ad51e00c8f | |||
| 195ec514c3 | |||
| 436db6c02d | |||
| cd13d479ee | |||
| 6516eadc60 | |||
| dce198c405 | |||
| 2a240b4a10 | |||
| 9249fc6ed0 | |||
| 9a42dfe73d | |||
| 84ea69411b | |||
| dc15fe7db8 | |||
| 6cda4ebc14 | |||
| d3e1fe3a1c | |||
| 9a76ccbfda | |||
| b6c17138bf | |||
| 382adf1042 | |||
| 870f9503c2 | |||
| b67f98141b | |||
| 2a609fc85d | |||
| 2b52bf895c | |||
| eaaecd128c | |||
| 78bf49adb4 | |||
| f024e9bd43 | |||
| 1b73cb828e | |||
| 7600d06651 | |||
| b365a88a52 | |||
| fa74bcaa4a | |||
| ad56e58330 | |||
| 66e807623b | |||
| 553d1aedde | |||
| 9ffc3b0d9a | |||
| 02283833a1 | |||
| acb22ac368 | |||
| e1a3d681c8 | |||
| fc0a045069 | |||
| 8f0569f3fd | |||
| 3a39425ab2 | |||
| 49d229b90f | |||
| f5670636f6 | |||
| 9d3c7949fd | |||
| 4852318ece | |||
| 6fdbcd7fae | |||
| 0bdca802eb | |||
| 9b65d9788d | |||
| b3af6c1f5f | |||
| f3a0e8d88c | |||
| ffd89807bf | |||
| da73ca1759 |
16
.gitattributes
vendored
Normal file
@ -0,0 +1,16 @@
|
|||||||
|
* text=auto
|
||||||
|
|
||||||
|
*.js text
|
||||||
|
*.md text
|
||||||
|
*.yml text
|
||||||
|
*.txt text
|
||||||
|
*.sh text
|
||||||
|
## *.bat text eol=crlf
|
||||||
|
*.bat -text
|
||||||
|
|
||||||
|
*.png binary
|
||||||
|
|
||||||
|
.gitattributes export-ignore
|
||||||
|
*.yml export-ignore
|
||||||
|
/wikipiki export-ignore
|
||||||
|
/.github export-ignore
|
||||||
18
.github/ISSUE_TEMPLATE/tools.md
vendored
Normal file
@ -0,0 +1,18 @@
|
|||||||
|
---
|
||||||
|
name: Tools
|
||||||
|
about: Report issues with the updaters, the troubleshooter, or any other tools.
|
||||||
|
title: ''
|
||||||
|
labels: ''
|
||||||
|
assignees: ''
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
<!--
|
||||||
|
Please specify:
|
||||||
|
- the name of the file (i.e. updater.bat, updater.sh)
|
||||||
|
- steps to reproduce the issue
|
||||||
|
- actual result
|
||||||
|
- expected result
|
||||||
|
|
||||||
|
Blank out this field before typing, or start typing after the next line.
|
||||||
|
-->
|
||||||
31
.github/ISSUE_TEMPLATE/troubleshooting-help.md
vendored
Normal file
@ -0,0 +1,31 @@
|
|||||||
|
---
|
||||||
|
name: Troubleshooting help
|
||||||
|
about: Ask for help to solve problems with user.js
|
||||||
|
title: 'follow instructions or this will be closed as invalid'
|
||||||
|
labels: ''
|
||||||
|
assignees: ''
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
<!--
|
||||||
|
|
||||||
|
Issues will be closed as invalid if you do not troubleshoot first, or if you ignore the required info in the template.
|
||||||
|
|
||||||
|
We do not support forks or no-longer supported releases.
|
||||||
|
|
||||||
|
-->
|
||||||
|
|
||||||
|
|
||||||
|
🟥 https://github.com/arkenfox/user.js/wiki/5.2-Troubleshooting
|
||||||
|
- [ ] I have read the troubleshooting guide, done the checks and confirmed this is caused by arkenfox
|
||||||
|
- _unchecked issues ~~may~~ will be closed as invalid_
|
||||||
|
|
||||||
|
🟪 REQUIRED INFO
|
||||||
|
- Browser version & OS:
|
||||||
|
- Steps to Reproduce (STR):
|
||||||
|
- Expected result:
|
||||||
|
- Actual result:
|
||||||
|
- Console errors and warnings:
|
||||||
|
- Anything else you deem worth mentioning:
|
||||||
|
|
||||||
|
---
|
||||||
15
.github/ISSUE_TEMPLATE/user-js.md
vendored
Normal file
@ -0,0 +1,15 @@
|
|||||||
|
---
|
||||||
|
name: user.js
|
||||||
|
about: Suggest changes to user.js
|
||||||
|
title: ''
|
||||||
|
labels: ''
|
||||||
|
assignees: ''
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
We value feedback in general, but we value feedback from informed users more. There is no need for you to be an expert to participate (most of us aren't), but we hope that you at least understand our decisions before questioning them. We discuss all changes openly, and we do not make changes lightly. So, if you don't understand why we decided to add/remove/change a certain pref, search the repo. The answer is most certainly here.
|
||||||
|
|
||||||
|
If some change we made took you by surprise (in the wrong way), remember that keeping track of changes is your responsibility. Watch the repo, read the [changelogs](https://github.com/arkenfox/user.js/issues?utf8=✓&q=is%3Aissue+label%3Achangelog), compare [releases](https://github.com/arkenfox/user.js/releases) as you update your copy of user.js, or use any other method you prefer.
|
||||||
|
|
||||||
|
Clear all of this when you're ready to type.
|
||||||
|
|
||||||
@ -1,6 +1,6 @@
|
|||||||
MIT License
|
MIT License
|
||||||
|
|
||||||
Copyright (c) 2017 ghacksuserjs
|
Copyright (c) 2020 arkenfox
|
||||||
|
|
||||||
Permission is hereby granted, free of charge, to any person obtaining a copy
|
Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||||
of this software and associated documentation files (the "Software"), to deal
|
of this software and associated documentation files (the "Software"), to deal
|
||||||
|
|||||||
45
README.md
@ -1,35 +1,26 @@
|
|||||||
###  user.js
|
### 🟪 user.js
|
||||||
A `user.js` is a configuration file that can control hundreds of Firefox settings. For a more technical breakdown and explanation, you can read more on the [overview](https://github.com/ghacksuserjs/ghacks-user.js/wiki/1.1-Overview) wiki page.
|
A `user.js` is a configuration file that can control Firefox settings - for a more technical breakdown and explanation, you can read more in the [wiki](https://github.com/arkenfox/user.js/wiki/2.1-User.js)
|
||||||
|
|
||||||
###  ghacks user.js
|
### 🟩 the arkenfox user.js
|
||||||
The [ghacks user.js](https://github.com/ghacksuserjs/ghacks-user.js/blob/master/user.js) is a template, which, as provided, aims (with [add-ons](https://github.com/ghacksuserjs/ghacks-user.js/wiki/Appendix-B:-Firefox-Add-ons)) to provide as much privacy and enhanced security as possible, and to reduce tracking and fingerprinting as much as possible - while minimizing any loss of functionality and breakage (but it will happen).
|
|
||||||
|
|
||||||
We aim to INFORM and give you CHOICES. No one size fits all, so customize it! And not all sites have the same requirements, so use [profiles](https://github.com/ghacksuserjs/ghacks-user.js/wiki/2.3-Concurrent-Profiles) with custom versions. We won't set you wrong.
|
[](https://opensource.org/licenses/MIT)
|
||||||
|
|
||||||
INFORMATION IS POWER. So you can make informed decisions to better protect yourself online, we aim to be:
|
The `arkenfox user.js` is a **template** which aims to provide as much privacy and enhanced security as possible, and to reduce tracking and fingerprinting as much as possible - while minimizing any loss of functionality and breakage (but it will happen).
|
||||||
|
|
||||||
* Accessible (provide information and simpler, less-technical descriptions if possible)
|
Everyone, experts included, should at least read the [wiki](https://github.com/arkenfox/user.js/wiki), as it contains important information regarding a few `user.js` settings. There is also an [interactive current release](https://arkenfox.github.io/gui/), thanks to [icpantsparti2](https://github.com/icpantsparti2).
|
||||||
* Accountable (provide reputable references/sources, [test sites](https://github.com/ghacksuserjs/ghacks-user.js/wiki/Appendix-C:-Test-Sites), dispel bad advice)
|
|
||||||
* Change trackable (yay! we're on github now, with commits)
|
|
||||||
* Compatible (including a deprecated section, [releases](https://github.com/ghacksuserjs/ghacks-user.js/releases))
|
|
||||||
* Comprehensive (including enforcing defaults and future-proofing)
|
|
||||||
* Current and up-to-date with stable (including [changelogs](https://github.com/ghacksuserjs/ghacks-user.js/search?q=label%3Achangelog&type=Issues&utf8=%E2%9C%93))
|
|
||||||
* Detailed (preference versioning, hidden preference information, explanations, and more)
|
|
||||||
* Easy to use and discuss (sections, sub-sections, numbering)
|
|
||||||
* Helpful (including a [wiki](https://github.com/ghacksuserjs/ghacks-user.js/wiki) with features such as [add-ons](https://github.com/ghacksuserjs/ghacks-user.js/wiki/Appendix-B:-Firefox-Add-ons), [user scripts](https://github.com/ghacksuserjs/ghacks-user.js/wiki/3.1-User-Scripts), [references](https://github.com/ghacksuserjs/ghacks-user.js/wiki/Appendix-D:-References) and more)
|
|
||||||
* Innovative (formatting, special tags, and future plans such as branches)
|
|
||||||
|
|
||||||
###  usage
|
Note that we do *not* recommend connecting over Tor on Firefox. Use the [Tor Browser](https://www.torproject.org/projects/torbrowser.html.en) if your [threat model](https://2019.www.torproject.org/about/torusers.html) calls for it, or for accessing hidden services.
|
||||||
Everyone, experts included, should at least read the [implementation](https://github.com/ghacksuserjs/ghacks-user.js/wiki/1.3-Implementation) wiki page, as it contains important information regarding a few default settings we use. The rest of the [wiki](https://github.com/ghacksuserjs/ghacks-user.js/wiki) is helpful as well.
|
|
||||||
|
|
||||||
###  acknowledgments
|
Also be aware that the `arkenfox user.js` is made specifically for desktop Firefox. Using it as-is in other Gecko-based browsers can be counterproductive, especially in the Tor Browser.
|
||||||
Literally thousands of sources, references and suggestions. That said...
|
|
||||||
|
|
||||||
* Martin Brinkmann at [ghacks](https://www.ghacks.net/) <sup>1</sup>
|
### 🟧 sitemap
|
||||||
* 100% genuine super-nice all-round good guy
|
|
||||||
* The ghacks community and commentators
|
|
||||||
* Special mentions to [earthlng](https://github.com/earthlng), Tom Hawack, Just me, Conker, Rockin’ Jerry, Ainatar, Parker Lewis
|
|
||||||
* [12bytes](http://12bytes.org/articles/tech/firefoxgecko-configuration-guide-for-privacy-and-performance-buffs)
|
|
||||||
* The 12bytes article now uses this user.js and supplements it with an additonal JS hosted right [here](https://github.com/atomGit/Firefox-user.js) at github
|
|
||||||
|
|
||||||
<sup>1</sup> The ghacks user.js was an independent project by [Thorin-Oakenpants](https://github.com/Thorin-Oakenpants) started in early 2015 and was [first published](https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/) at ghacks in August 2015. It was kept up-to-date and expanded by the original author with three major updates and articles. With Martin Brinkmann's blessing, it will keep the ghacks name.
|
- [releases](https://github.com/arkenfox/user.js/releases)
|
||||||
|
- [changelogs](https://github.com/arkenfox/user.js/issues?utf8=%E2%9C%93&q=is%3Aissue+label%3Achangelog)
|
||||||
|
- [wiki](https://github.com/arkenfox/user.js/wiki)
|
||||||
|
- [stickies](https://github.com/arkenfox/user.js/issues?q=is%3Aissue+is%3Aopen+label%3A%22sticky+topic%22)
|
||||||
|
- [diffs](https://github.com/arkenfox/user.js/issues?q=is%3Aissue+label%3Adiffs)
|
||||||
|
- [common questions and answers](https://github.com/arkenfox/user.js/issues?q=is%3Aissue+label%3Aanswered)
|
||||||
|
|
||||||
|
### 🟥 acknowledgments
|
||||||
|
Literally thousands of sources, references and suggestions. Many thanks, and much appreciated.
|
||||||
|
|||||||
@ -1 +1,3 @@
|
|||||||
theme: jekyll-theme-midnight
|
theme: jekyll-theme-midnight
|
||||||
|
title: user.js
|
||||||
|
description: An ongoing comprehensive user.js template for configuring and hardening Firefox privacy, security and anti-fingerprinting
|
||||||
|
|||||||
133
prefsCleaner.bat
Normal file
@ -0,0 +1,133 @@
|
|||||||
|
@ECHO OFF & SETLOCAL DisableDelayedExpansion
|
||||||
|
TITLE prefs.js cleaner
|
||||||
|
|
||||||
|
REM ### prefs.js cleaner for Windows
|
||||||
|
REM ## author: @claustromaniac
|
||||||
|
REM ## version: 2.8
|
||||||
|
|
||||||
|
CD /D "%~dp0"
|
||||||
|
|
||||||
|
IF /I "%~1"=="-unattended" (SET _ua=1)
|
||||||
|
|
||||||
|
:begin
|
||||||
|
ECHO:
|
||||||
|
ECHO:
|
||||||
|
ECHO ########################################
|
||||||
|
ECHO #### prefs.js cleaner for Windows ####
|
||||||
|
ECHO #### by claustromaniac ####
|
||||||
|
ECHO #### v2.8 ####
|
||||||
|
ECHO ########################################
|
||||||
|
ECHO:
|
||||||
|
CALL :message "This script should be run from your Firefox profile directory."
|
||||||
|
ECHO It will remove any entries from prefs.js that also exist in user.js.
|
||||||
|
CALL :message "This will allow inactive preferences to be reset to their default values."
|
||||||
|
ECHO This Firefox profile shouldn't be in use during the process.
|
||||||
|
CALL :message ""
|
||||||
|
TIMEOUT 1 /nobreak >nul
|
||||||
|
|
||||||
|
IF NOT DEFINED _ua (
|
||||||
|
CHOICE /C SHE /N /M "Start [S] Help [H] Exit [E]"
|
||||||
|
CLS
|
||||||
|
IF ERRORLEVEL 3 (EXIT /B)
|
||||||
|
IF ERRORLEVEL 2 (GOTO :showhelp)
|
||||||
|
)
|
||||||
|
IF NOT EXIST "user.js" (CALL :abort "user.js not found in the current directory." 30)
|
||||||
|
IF NOT EXIST "prefs.js" (CALL :abort "prefs.js not found in the current directory." 30)
|
||||||
|
CALL :strlenCheck
|
||||||
|
CALL :FFcheck
|
||||||
|
|
||||||
|
CALL :message "Backing up prefs.js..."
|
||||||
|
FOR /F "delims=" %%# IN ('powershell -command get-date -format "{yyyyMMdd_HHmmss}"') DO @SET ldt=%%#
|
||||||
|
COPY /B /V /Y prefs.js "prefs-backup-%ldt%.js"
|
||||||
|
|
||||||
|
CALL :message "Cleaning prefs.js..."
|
||||||
|
CALL :cleanup
|
||||||
|
CALL :message "All done!"
|
||||||
|
TIMEOUT 5 >nul
|
||||||
|
ENDLOCAL
|
||||||
|
EXIT /B
|
||||||
|
|
||||||
|
REM ########## Abort Function ###########
|
||||||
|
:abort
|
||||||
|
CALL :message %1
|
||||||
|
TIMEOUT %~2 >nul
|
||||||
|
EXIT
|
||||||
|
REM ########## Message Function #########
|
||||||
|
:message
|
||||||
|
ECHO:
|
||||||
|
ECHO: %~1
|
||||||
|
ECHO:
|
||||||
|
GOTO :EOF
|
||||||
|
REM ### string length Check Function ####
|
||||||
|
:strlenCheck
|
||||||
|
SET /a cnt=0
|
||||||
|
setlocal ENABLEDELAYEDEXPANSION
|
||||||
|
FOR /F "tokens=1,* delims=:" %%G IN ('FINDSTR /N "^" prefs.js') DO (
|
||||||
|
ECHO:%%H >nul
|
||||||
|
SET /a cnt += 1
|
||||||
|
IF /I "%%G" NEQ "!cnt!" (
|
||||||
|
ECHO:
|
||||||
|
CALL :message "ERROR: line !cnt! in prefs.js is too long."
|
||||||
|
(CALL :abort "Aborting ..." 30)
|
||||||
|
)
|
||||||
|
)
|
||||||
|
endlocal
|
||||||
|
GOTO :EOF
|
||||||
|
REM ####### Firefox Check Function ######
|
||||||
|
:FFcheck
|
||||||
|
TASKLIST /FI "IMAGENAME eq firefox.exe" 2>NUL | FIND /I /N "firefox.exe">NUL
|
||||||
|
IF NOT ERRORLEVEL 1 (
|
||||||
|
CLS
|
||||||
|
CALL :message "Firefox is still running."
|
||||||
|
ECHO If you're not currently using this profile you can continue, otherwise
|
||||||
|
CALL :message "close Firefox first!"
|
||||||
|
ECHO:
|
||||||
|
PAUSE
|
||||||
|
CLS
|
||||||
|
CALL :message "Resuming..."
|
||||||
|
TIMEOUT 5 /nobreak >nul
|
||||||
|
)
|
||||||
|
GOTO :EOF
|
||||||
|
REM ######### Cleanup Function ##########
|
||||||
|
:cleanup
|
||||||
|
FOR /F tokens^=2^ delims^=^'^" %%G IN ('FINDSTR /R /C:"^[^\"']*user_pref[ ]*\([ ]*[\"'][^\"']*[\"'][ ]*," user.js') DO (
|
||||||
|
IF NOT ""=="%%G" (SET "[%%G]=1")
|
||||||
|
)
|
||||||
|
(
|
||||||
|
FOR /F "tokens=1,* delims=:" %%G IN ('FINDSTR /N "^" prefs.js') DO (
|
||||||
|
IF ""=="%%H" (
|
||||||
|
ECHO:
|
||||||
|
) ELSE (
|
||||||
|
FOR /F tokens^=1^,2^ delims^=^"^' %%I IN ("%%H") DO (
|
||||||
|
IF NOT DEFINED [%%J] (ECHO:%%H)
|
||||||
|
)
|
||||||
|
)
|
||||||
|
)
|
||||||
|
)>tempcleanedprefs
|
||||||
|
MOVE /Y tempcleanedprefs prefs.js
|
||||||
|
GOTO :EOF
|
||||||
|
REM ############### Help ##################
|
||||||
|
:showhelp
|
||||||
|
MODE 80,34
|
||||||
|
CLS
|
||||||
|
CALL :message "This script creates a backup of your prefs.js file before doing anything."
|
||||||
|
ECHO It should be safe, but you can follow these steps if something goes wrong:
|
||||||
|
ECHO:
|
||||||
|
CALL :message " 1. Make sure Firefox is closed."
|
||||||
|
ECHO 2. Delete prefs.js in your profile folder.
|
||||||
|
CALL :message " 3. Delete Invalidprefs.js if you have one in the same folder."
|
||||||
|
ECHO 4. Rename or copy your latest backup to prefs.js.
|
||||||
|
CALL :message " 5. Run Firefox and see if you notice anything wrong with it."
|
||||||
|
ECHO 6. If you do notice something wrong, especially with your extensions,
|
||||||
|
CALL :message " and/or with the UI, go to about:support, and restart Firefox with"
|
||||||
|
ECHO add-ons disabled. Then, restart it again normally, and see if the
|
||||||
|
CALL :message " problems were solved."
|
||||||
|
ECHO:
|
||||||
|
CALL :message "If you are able to identify the cause of your issues, please bring it up"
|
||||||
|
ECHO on arkenfox user.js GitHub repository.
|
||||||
|
ECHO:
|
||||||
|
ECHO:
|
||||||
|
PAUSE
|
||||||
|
CLS
|
||||||
|
GOTO :begin
|
||||||
|
REM #####################################
|
||||||
185
prefsCleaner.sh
Executable file
@ -0,0 +1,185 @@
|
|||||||
|
#!/usr/bin/env bash
|
||||||
|
|
||||||
|
## prefs.js cleaner for Linux/Mac
|
||||||
|
## author: @claustromaniac
|
||||||
|
## version: 2.1
|
||||||
|
|
||||||
|
## special thanks to @overdodactyl and @earthlng for a few snippets that I stol..*cough* borrowed from the updater.sh
|
||||||
|
|
||||||
|
## DON'T GO HIGHER THAN VERSION x.9 !! ( because of ASCII comparison in update_prefsCleaner() )
|
||||||
|
|
||||||
|
readonly CURRDIR=$(pwd)
|
||||||
|
|
||||||
|
## get the full path of this script (readlink for Linux, greadlink for Mac with coreutils installed)
|
||||||
|
SCRIPT_FILE=$(readlink -f "${BASH_SOURCE[0]}" 2>/dev/null || greadlink -f "${BASH_SOURCE[0]}" 2>/dev/null)
|
||||||
|
|
||||||
|
## fallback for Macs without coreutils
|
||||||
|
[ -z "$SCRIPT_FILE" ] && SCRIPT_FILE=${BASH_SOURCE[0]}
|
||||||
|
|
||||||
|
|
||||||
|
AUTOUPDATE=true
|
||||||
|
QUICKSTART=false
|
||||||
|
|
||||||
|
## download method priority: curl -> wget
|
||||||
|
DOWNLOAD_METHOD=''
|
||||||
|
if command -v curl >/dev/null; then
|
||||||
|
DOWNLOAD_METHOD='curl --max-redirs 3 -so'
|
||||||
|
elif command -v wget >/dev/null; then
|
||||||
|
DOWNLOAD_METHOD='wget --max-redirect 3 --quiet -O'
|
||||||
|
else
|
||||||
|
AUTOUPDATE=false
|
||||||
|
echo -e "No curl or wget detected.\nAutomatic self-update disabled!"
|
||||||
|
fi
|
||||||
|
|
||||||
|
fQuit() {
|
||||||
|
## change directory back to the original working directory
|
||||||
|
cd "${CURRDIR}"
|
||||||
|
[ "$1" -eq 0 ] && echo -e "\n$2" || echo -e "\n$2" >&2
|
||||||
|
exit $1
|
||||||
|
}
|
||||||
|
|
||||||
|
fUsage() {
|
||||||
|
echo -e "\nUsage: $0 [-ds]"
|
||||||
|
echo -e "
|
||||||
|
Optional Arguments:
|
||||||
|
-s Start immediately
|
||||||
|
-d Don't auto-update prefsCleaner.sh"
|
||||||
|
}
|
||||||
|
|
||||||
|
download_file() { # expects URL as argument ($1)
|
||||||
|
declare -r tf=$(mktemp)
|
||||||
|
|
||||||
|
$DOWNLOAD_METHOD "${tf}" "$1" &>/dev/null && echo "$tf" || echo '' # return the temp-filename or empty string on error
|
||||||
|
}
|
||||||
|
|
||||||
|
fFF_check() {
|
||||||
|
# there are many ways to see if firefox is running or not, some more reliable than others
|
||||||
|
# this isn't elegant and might not be future-proof but should at least be compatible with any environment
|
||||||
|
while [ -e lock ]; do
|
||||||
|
echo -e "\nThis Firefox profile seems to be in use. Close Firefox and try again.\n" >&2
|
||||||
|
read -r -p "Press any key to continue."
|
||||||
|
done
|
||||||
|
}
|
||||||
|
|
||||||
|
## returns the version number of a prefsCleaner.sh file
|
||||||
|
get_prefsCleaner_version() {
|
||||||
|
echo "$(sed -n '5 s/.*[[:blank:]]\([[:digit:]]*\.[[:digit:]]*\)/\1/p' "$1")"
|
||||||
|
}
|
||||||
|
|
||||||
|
## updates the prefsCleaner.sh file based on the latest public version
|
||||||
|
update_prefsCleaner() {
|
||||||
|
declare -r tmpfile="$(download_file 'https://raw.githubusercontent.com/arkenfox/user.js/master/prefsCleaner.sh')"
|
||||||
|
[ -z "$tmpfile" ] && echo -e "Error! Could not download prefsCleaner.sh" && return 1 # check if download failed
|
||||||
|
|
||||||
|
[[ $(get_prefsCleaner_version "$SCRIPT_FILE") == $(get_prefsCleaner_version "$tmpfile") ]] && return 0
|
||||||
|
|
||||||
|
mv "$tmpfile" "$SCRIPT_FILE"
|
||||||
|
chmod u+x "$SCRIPT_FILE"
|
||||||
|
"$SCRIPT_FILE" "$@" -d
|
||||||
|
exit 0
|
||||||
|
}
|
||||||
|
|
||||||
|
fClean() {
|
||||||
|
# the magic happens here
|
||||||
|
prefs="@@"
|
||||||
|
prefexp="user_pref[ ]*\([ ]*[\"']([^\"']+)[\"'][ ]*,"
|
||||||
|
while read -r line; do
|
||||||
|
if [[ "$line" =~ $prefexp && $prefs != *"@@${BASH_REMATCH[1]}@@"* ]]; then
|
||||||
|
prefs="${prefs}${BASH_REMATCH[1]}@@"
|
||||||
|
fi
|
||||||
|
done <<< "$(grep -E "$prefexp" user.js)"
|
||||||
|
|
||||||
|
while IFS='' read -r line || [[ -n "$line" ]]; do
|
||||||
|
if [[ "$line" =~ ^$prefexp ]]; then
|
||||||
|
if [[ $prefs != *"@@${BASH_REMATCH[1]}@@"* ]]; then
|
||||||
|
echo "$line"
|
||||||
|
fi
|
||||||
|
else
|
||||||
|
echo "$line"
|
||||||
|
fi
|
||||||
|
done < "$1" > prefs.js
|
||||||
|
}
|
||||||
|
|
||||||
|
fStart() {
|
||||||
|
if [ ! -e user.js ]; then
|
||||||
|
fQuit 1 "user.js not found in the current directory."
|
||||||
|
elif [ ! -e prefs.js ]; then
|
||||||
|
fQuit 1 "prefs.js not found in the current directory."
|
||||||
|
fi
|
||||||
|
|
||||||
|
fFF_check
|
||||||
|
mkdir -p prefsjs_backups
|
||||||
|
bakfile="prefsjs_backups/prefs.js.backup.$(date +"%Y-%m-%d_%H%M")"
|
||||||
|
mv prefs.js "${bakfile}" || fQuit 1 "Operation aborted.\nReason: Could not create backup file $bakfile"
|
||||||
|
echo -e "\nprefs.js backed up: $bakfile"
|
||||||
|
echo "Cleaning prefs.js..."
|
||||||
|
fClean "$bakfile"
|
||||||
|
fQuit 0 "All done!"
|
||||||
|
}
|
||||||
|
|
||||||
|
|
||||||
|
while getopts "sd" opt; do
|
||||||
|
case $opt in
|
||||||
|
s)
|
||||||
|
QUICKSTART=true
|
||||||
|
;;
|
||||||
|
d)
|
||||||
|
AUTOUPDATE=false
|
||||||
|
;;
|
||||||
|
esac
|
||||||
|
done
|
||||||
|
|
||||||
|
## change directory to the Firefox profile directory
|
||||||
|
cd "$(dirname "${SCRIPT_FILE}")"
|
||||||
|
|
||||||
|
# Check if running as root and if any files have the owner as root/wheel.
|
||||||
|
if [ "${EUID:-"$(id -u)"}" -eq 0 ]; then
|
||||||
|
fQuit 1 "You shouldn't run this with elevated privileges (such as with doas/sudo)."
|
||||||
|
elif [ -n "$(find ./ -user 0)" ]; then
|
||||||
|
printf 'It looks like this script was previously run with elevated privileges,
|
||||||
|
you will need to change ownership of the following files to your user:\n'
|
||||||
|
find . -user 0
|
||||||
|
fQuit 1
|
||||||
|
fi
|
||||||
|
|
||||||
|
[ "$AUTOUPDATE" = true ] && update_prefsCleaner "$@"
|
||||||
|
|
||||||
|
echo -e "\n\n"
|
||||||
|
echo " ╔══════════════════════════╗"
|
||||||
|
echo " ║ prefs.js cleaner ║"
|
||||||
|
echo " ║ by claustromaniac ║"
|
||||||
|
echo " ║ v2.1 ║"
|
||||||
|
echo " ╚══════════════════════════╝"
|
||||||
|
echo -e "\nThis script should be run from your Firefox profile directory.\n"
|
||||||
|
echo "It will remove any entries from prefs.js that also exist in user.js."
|
||||||
|
echo "This will allow inactive preferences to be reset to their default values."
|
||||||
|
echo -e "\nThis Firefox profile shouldn't be in use during the process.\n"
|
||||||
|
|
||||||
|
[ "$QUICKSTART" = true ] && fStart
|
||||||
|
|
||||||
|
echo -e "\nIn order to proceed, select a command below by entering its corresponding number.\n"
|
||||||
|
|
||||||
|
select option in Start Help Exit; do
|
||||||
|
case $option in
|
||||||
|
Start)
|
||||||
|
fStart
|
||||||
|
;;
|
||||||
|
Help)
|
||||||
|
fUsage
|
||||||
|
echo -e "\nThis script creates a backup of your prefs.js file before doing anything."
|
||||||
|
echo -e "It should be safe, but you can follow these steps if something goes wrong:\n"
|
||||||
|
echo "1. Make sure Firefox is closed."
|
||||||
|
echo "2. Delete prefs.js in your profile folder."
|
||||||
|
echo "3. Delete Invalidprefs.js if you have one in the same folder."
|
||||||
|
echo "4. Rename or copy your latest backup to prefs.js."
|
||||||
|
echo "5. Run Firefox and see if you notice anything wrong with it."
|
||||||
|
echo "6. If you do notice something wrong, especially with your extensions, and/or with the UI, go to about:support, and restart Firefox with add-ons disabled. Then, restart it again normally, and see if the problems were solved."
|
||||||
|
echo -e "If you are able to identify the cause of your issues, please bring it up on the arkenfox user.js GitHub repository.\n"
|
||||||
|
;;
|
||||||
|
Exit)
|
||||||
|
fQuit 0
|
||||||
|
;;
|
||||||
|
esac
|
||||||
|
done
|
||||||
|
|
||||||
|
fQuit 0
|
||||||
166
scratchpad-scripts/arkenfox-cleanup.js
Normal file
@ -0,0 +1,166 @@
|
|||||||
|
/***
|
||||||
|
This will reset the preferences that since FF91 have been
|
||||||
|
- removed from the arkenfox user.js
|
||||||
|
- deprecated by Mozilla but listed in the arkenfox user.js in the past
|
||||||
|
|
||||||
|
There is an archived version at https://github.com/arkenfox/user.js/issues/123
|
||||||
|
if you want the full list since jesus
|
||||||
|
|
||||||
|
Last updated: 21-April-2025
|
||||||
|
|
||||||
|
Instructions:
|
||||||
|
- [optional] close Firefox and backup your profile
|
||||||
|
- [optional] disable your network connection [1]
|
||||||
|
- start Firefox
|
||||||
|
- load about:config and press Ctrl+Shift+K to open the Web Console for about:config
|
||||||
|
- using about:config is important, so the script has the right permissions
|
||||||
|
- paste this script
|
||||||
|
- if you edited the list of prefs in the script, make sure the last pref does not have a trailing comma
|
||||||
|
- hit enter
|
||||||
|
- check the Info output to see which prefs were reset
|
||||||
|
- restart
|
||||||
|
- some prefs require a restart
|
||||||
|
- a restart will reapply your user.js
|
||||||
|
- [optional] re-enable your network connection
|
||||||
|
|
||||||
|
[1] Blocking Firefox from the internet ensures it cannot act on your reset preferences in the
|
||||||
|
period before you restart it, such as app and extension auto-updating, or downloading unwanted
|
||||||
|
components (GMP etc). It depends on what you're resetting and how long before you restart.
|
||||||
|
|
||||||
|
***/
|
||||||
|
|
||||||
|
(() => {
|
||||||
|
|
||||||
|
if ('undefined' === typeof(Services)) return alert('about:config needs to be the active tab!');
|
||||||
|
|
||||||
|
const aPREFS = [
|
||||||
|
/* DEPRECATED */
|
||||||
|
/* 129-140 */
|
||||||
|
'media.ondevicechange.enabled', // 137
|
||||||
|
'webchannel.allowObject.urlWhitelist', // 132
|
||||||
|
/* 116-128 */
|
||||||
|
'browser.contentanalysis.default_allow', // 127
|
||||||
|
'browser.messaging-system.whatsNewPanel.enabled', // 126
|
||||||
|
'browser.ping-centre.telemetry', // 123
|
||||||
|
'dom.webnotifications.serviceworker.enabled', // 117
|
||||||
|
'javascript.use_us_english_locale', // 119
|
||||||
|
'layout.css.font-visibility.private', // 118
|
||||||
|
'layout.css.font-visibility.resistFingerprinting', // 116
|
||||||
|
'layout.css.font-visibility.standard', // 118
|
||||||
|
'layout.css.font-visibility.trackingprotection', // 118
|
||||||
|
'network.dns.skipTRR-when-parental-control-enabled', // 119
|
||||||
|
'permissions.delegation.enabled', // 118
|
||||||
|
'security.family_safety.mode', // 117
|
||||||
|
'widget.non-native-theme.enabled', // 127
|
||||||
|
/* 103-115 */
|
||||||
|
'browser.cache.offline.enable', // 115
|
||||||
|
'extensions.formautofill.heuristics.enabled', // 114
|
||||||
|
'network.cookie.lifetimePolicy', // 103 [technically removed in 104]
|
||||||
|
'privacy.clearsitedata.cache.enabled', // 114
|
||||||
|
'privacy.resistFingerprinting.testGranularityMask', // 114
|
||||||
|
'security.pki.sha1_enforcement_level', // 103
|
||||||
|
/* 92-102 */
|
||||||
|
'browser.urlbar.suggest.quicksuggest', // 95
|
||||||
|
'dom.securecontext.whitelist_onions', // 97
|
||||||
|
'dom.storage.next_gen', // 102
|
||||||
|
'network.http.spdy.enabled', // 100
|
||||||
|
'network.http.spdy.enabled.deps',
|
||||||
|
'network.http.spdy.enabled.http2',
|
||||||
|
'network.http.spdy.websockets',
|
||||||
|
'layout.css.font-visibility.level', // 94
|
||||||
|
'security.ask_for_password', // 102
|
||||||
|
'security.csp.enable', // 99
|
||||||
|
'security.password_lifetime', // 102
|
||||||
|
'security.ssl3.rsa_des_ede3_sha', // 93
|
||||||
|
|
||||||
|
/* REMOVED */
|
||||||
|
/* 129-140 */
|
||||||
|
'dom.securecontext.allowlist_onions',
|
||||||
|
'network.http.referer.hideOnionSource',
|
||||||
|
'privacy.clearOnShutdown.cache',
|
||||||
|
'privacy.clearOnShutdown.cookies',
|
||||||
|
'privacy.clearOnShutdown.downloads',
|
||||||
|
'privacy.clearOnShutdown.formdata',
|
||||||
|
'privacy.clearOnShutdown.history',
|
||||||
|
'privacy.clearOnShutdown.offlineApps',
|
||||||
|
'privacy.clearOnShutdown.sessions',
|
||||||
|
'privacy.cpd.cache',
|
||||||
|
'privacy.cpd.cookies',
|
||||||
|
'privacy.cpd.formdata',
|
||||||
|
'privacy.cpd.history',
|
||||||
|
'privacy.cpd.offlineApps',
|
||||||
|
'privacy.cpd.sessions',
|
||||||
|
/* 116-128 */
|
||||||
|
'browser.fixup.alternate.enabled',
|
||||||
|
'browser.taskbar.previews.enable',
|
||||||
|
'browser.urlbar.dnsResolveSingleWordsAfterSearch',
|
||||||
|
'geo.provider.network.url',
|
||||||
|
'geo.provider.network.logging.enabled',
|
||||||
|
'geo.provider.use_gpsd',
|
||||||
|
'media.gmp-widevinecdm.enabled',
|
||||||
|
'network.protocol-handler.external.ms-windows-store',
|
||||||
|
'privacy.partition.always_partition_third_party_non_cookie_storage',
|
||||||
|
'privacy.partition.always_partition_third_party_non_cookie_storage.exempt_sessionstorage',
|
||||||
|
'privacy.partition.serviceWorkers',
|
||||||
|
/* 103-115 */
|
||||||
|
'beacon.enabled',
|
||||||
|
'browser.startup.blankWindow',
|
||||||
|
'browser.newtab.preload',
|
||||||
|
'browser.newtabpage.activity-stream.feeds.discoverystreamfeed',
|
||||||
|
'browser.newtabpage.activity-stream.feeds.snippets',
|
||||||
|
'browser.region.network.url',
|
||||||
|
'browser.region.update.enabled',
|
||||||
|
'browser.search.region',
|
||||||
|
'browser.ssl_override_behavior',
|
||||||
|
'browser.tabs.warnOnClose',
|
||||||
|
'devtools.chrome.enabled',
|
||||||
|
'dom.disable_beforeunload',
|
||||||
|
'dom.disable_open_during_load',
|
||||||
|
'dom.netinfo.enabled',
|
||||||
|
'dom.vr.enabled',
|
||||||
|
'extensions.formautofill.addresses.supported',
|
||||||
|
'extensions.formautofill.available',
|
||||||
|
'extensions.formautofill.creditCards.available',
|
||||||
|
'extensions.formautofill.creditCards.supported',
|
||||||
|
'middlemouse.contentLoadURL',
|
||||||
|
'network.http.altsvc.oe',
|
||||||
|
/* 92-102 */
|
||||||
|
'browser.urlbar.trimURLs',
|
||||||
|
'dom.caches.enabled',
|
||||||
|
'dom.storageManager.enabled',
|
||||||
|
'dom.storage_access.enabled',
|
||||||
|
'dom.targetBlankNoOpener.enabled',
|
||||||
|
'network.cookie.thirdparty.sessionOnly',
|
||||||
|
'network.cookie.thirdparty.nonsecureSessionOnly',
|
||||||
|
'privacy.firstparty.isolate.block_post_message',
|
||||||
|
'privacy.firstparty.isolate.restrict_opener_access',
|
||||||
|
'privacy.firstparty.isolate.use_site',
|
||||||
|
'privacy.window.name.update.enabled',
|
||||||
|
'security.insecure_connection_text.enabled',
|
||||||
|
|
||||||
|
/* IMPORTANT: last active pref must not have a trailing comma */
|
||||||
|
/* reset parrot: check your open about:config after running the script */
|
||||||
|
'_user.js.parrot'
|
||||||
|
];
|
||||||
|
|
||||||
|
console.clear();
|
||||||
|
|
||||||
|
let c = 0;
|
||||||
|
for (const sPname of aPREFS) {
|
||||||
|
if (Services.prefs.prefHasUserValue(sPname)) {
|
||||||
|
Services.prefs.clearUserPref(sPname);
|
||||||
|
if (!Services.prefs.prefHasUserValue(sPname)) {
|
||||||
|
console.info('reset', sPname);
|
||||||
|
c++;
|
||||||
|
} else console.warn('failed to reset', sPname);
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
focus();
|
||||||
|
|
||||||
|
const d = (c==1) ? ' pref' : ' prefs';
|
||||||
|
alert(c ? 'successfully reset ' + c + d + "\n\nfor details check the console" : 'nothing to reset');
|
||||||
|
|
||||||
|
return 'all done';
|
||||||
|
|
||||||
|
})();
|
||||||
210
scratchpad-scripts/troubleshooter.js
Normal file
@ -0,0 +1,210 @@
|
|||||||
|
/*** arkenfox user.js troubleshooter.js v1.6.3 ***/
|
||||||
|
|
||||||
|
(function() {
|
||||||
|
|
||||||
|
if ("undefined" === typeof(Services)) return alert('about:config needs to be the active tab!');
|
||||||
|
|
||||||
|
const aPREFS = [
|
||||||
|
|
||||||
|
/* known culprits */
|
||||||
|
'network.cookie.cookieBehavior',
|
||||||
|
'network.http.referer.XOriginPolicy',
|
||||||
|
'privacy.firstparty.isolate',
|
||||||
|
'privacy.resistFingerprinting',
|
||||||
|
'security.mixed_content.block_display_content',
|
||||||
|
'svg.disabled',
|
||||||
|
|
||||||
|
/* Storage + Cache */
|
||||||
|
'browser.cache.offline.enable',
|
||||||
|
'dom.storage.enabled',
|
||||||
|
'dom.storageManager.enabled',
|
||||||
|
|
||||||
|
/* Workers, Web + Push Notifications */
|
||||||
|
'dom.caches.enabled',
|
||||||
|
'dom.push.connection.enabled',
|
||||||
|
'dom.push.enabled',
|
||||||
|
'dom.push.serverURL',
|
||||||
|
'dom.serviceWorkers.enabled',
|
||||||
|
'dom.webnotifications.enabled',
|
||||||
|
'dom.webnotifications.serviceworker.enabled',
|
||||||
|
|
||||||
|
/* Fonts */
|
||||||
|
'browser.display.use_document_fonts',
|
||||||
|
'font.blacklist.underline_offset',
|
||||||
|
'gfx.font_rendering.graphite.enabled',
|
||||||
|
'gfx.font_rendering.opentype_svg.enabled',
|
||||||
|
'layout.css.font-loading-api.enabled',
|
||||||
|
|
||||||
|
/* Misc */
|
||||||
|
'browser.link.open_newwindow.restriction',
|
||||||
|
'canvas.capturestream.enabled',
|
||||||
|
'dom.event.clipboardevents.enabled',
|
||||||
|
'dom.event.contextmenu.enabled',
|
||||||
|
'dom.IntersectionObserver.enabled',
|
||||||
|
'dom.popup_allowed_events',
|
||||||
|
'full-screen-api.enabled',
|
||||||
|
'intl.accept_languages',
|
||||||
|
'javascript.options.asmjs',
|
||||||
|
'javascript.options.wasm',
|
||||||
|
'permissions.default.shortcuts',
|
||||||
|
|
||||||
|
/* Hardware */
|
||||||
|
'dom.vr.enabled',
|
||||||
|
'media.ondevicechange.enabled',
|
||||||
|
|
||||||
|
/* Audio + Video */
|
||||||
|
'dom.webaudio.enabled',
|
||||||
|
'media.autoplay.default', // FF63+
|
||||||
|
'media.autoplay.blocking_policy', // FF78+
|
||||||
|
|
||||||
|
/* Forms */
|
||||||
|
'browser.formfill.enable',
|
||||||
|
'signon.autofillForms',
|
||||||
|
'signon.formlessCapture.enabled',
|
||||||
|
|
||||||
|
/* HTTPS */
|
||||||
|
'security.cert_pinning.enforcement_level',
|
||||||
|
'security.family_safety.mode',
|
||||||
|
'security.OCSP.require',
|
||||||
|
'security.pki.sha1_enforcement_level',
|
||||||
|
'security.ssl.require_safe_negotiation',
|
||||||
|
'security.ssl.treat_unsafe_negotiation_as_broken',
|
||||||
|
'security.ssl3.dhe_rsa_aes_128_sha',
|
||||||
|
'security.ssl3.dhe_rsa_aes_256_sha',
|
||||||
|
'security.ssl3.ecdhe_ecdsa_aes_128_sha',
|
||||||
|
'security.ssl3.ecdhe_rsa_aes_128_sha',
|
||||||
|
'security.ssl3.rsa_aes_128_sha',
|
||||||
|
'security.ssl3.rsa_aes_256_sha',
|
||||||
|
'security.ssl3.rsa_des_ede3_sha',
|
||||||
|
'security.tls.enable_0rtt_data',
|
||||||
|
'security.tls.version.max',
|
||||||
|
'security.tls.version.min',
|
||||||
|
|
||||||
|
/* Plugins + Flash */
|
||||||
|
'plugin.default.state',
|
||||||
|
'plugin.state.flash',
|
||||||
|
|
||||||
|
/* unlikely to cause problems */
|
||||||
|
'dom.popup_maximum',
|
||||||
|
'geo.provider.network.url',
|
||||||
|
'layout.css.visited_links_enabled',
|
||||||
|
'mathml.disabled',
|
||||||
|
'network.auth.subresource-http-auth-allow',
|
||||||
|
'network.http.redirection-limit',
|
||||||
|
'network.protocol-handler.external.ms-windows-store',
|
||||||
|
'privacy.trackingprotection.enabled',
|
||||||
|
'security.data_uri.block_toplevel_data_uri_navigations',
|
||||||
|
'privacy.window.name.update.enabled', // FF82+
|
||||||
|
|
||||||
|
'last.one.without.comma'
|
||||||
|
]
|
||||||
|
|
||||||
|
// any runtime-set pref that everyone will have and that can be safely reset
|
||||||
|
const oFILLER = { type: 64, name: 'app.update.lastUpdateTime.browser-cleanup-thumbnails', value: 1580000000 };
|
||||||
|
|
||||||
|
function getMyList(arr) {
|
||||||
|
const aRet = [];
|
||||||
|
for (const sPname of arr) {
|
||||||
|
if (Services.prefs.prefHasUserValue(sPname)) {
|
||||||
|
const ptype = Services.prefs.getPrefType(sPname);
|
||||||
|
switch (ptype) {
|
||||||
|
case 32: // string (see https://dxr.mozilla.org/mozilla-central/source/modules/libpref/nsIPrefBranch.idl#31)
|
||||||
|
aRet.push({'type':ptype,'name':sPname,'value':Services.prefs.getCharPref(sPname)});
|
||||||
|
break;
|
||||||
|
case 64: // int
|
||||||
|
aRet.push({'type':ptype,'name':sPname,'value':Services.prefs.getIntPref(sPname)});
|
||||||
|
break;
|
||||||
|
case 128: // boolean
|
||||||
|
aRet.push({'type':ptype,'name':sPname,'value':Services.prefs.getBoolPref(sPname)});
|
||||||
|
break;
|
||||||
|
default:
|
||||||
|
console.log("error detecting pref-type for '"+sPname+"' !");
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
return aRet;
|
||||||
|
}
|
||||||
|
|
||||||
|
function reapply(arr) {
|
||||||
|
for (const oPref of arr) {
|
||||||
|
switch (oPref.type) {
|
||||||
|
case 32: // string
|
||||||
|
Services.prefs.setCharPref(oPref.name, oPref.value);
|
||||||
|
break;
|
||||||
|
case 64: // int
|
||||||
|
Services.prefs.setIntPref(oPref.name, oPref.value);
|
||||||
|
break;
|
||||||
|
case 128: // boolean
|
||||||
|
Services.prefs.setBoolPref(oPref.name, oPref.value);
|
||||||
|
break;
|
||||||
|
default:
|
||||||
|
console.log("error re-appyling value for '"+oPref.name+"' !"); // should never happen
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
function myreset(arr) {
|
||||||
|
for (const oPref of arr) Services.prefs.clearUserPref(oPref.name);
|
||||||
|
}
|
||||||
|
|
||||||
|
function resetAllMatchingDefault(arr) {
|
||||||
|
const aTmp = getMyList(arr);
|
||||||
|
myreset(aTmp);
|
||||||
|
reapply(aTmp);
|
||||||
|
}
|
||||||
|
|
||||||
|
function _main(aALL) {
|
||||||
|
const _h = (arr) => Math.ceil(arr.length/2);
|
||||||
|
|
||||||
|
let aTmp = aALL, aDbg = aALL;
|
||||||
|
reapply(aALL);
|
||||||
|
myreset(aTmp.slice(0, _h(aTmp)));
|
||||||
|
while (aTmp.length) {
|
||||||
|
alert('NOW TEST AGAIN !');
|
||||||
|
if (confirm('if the problem still exists click OK, otherwise click Cancel.')) {
|
||||||
|
aTmp = aTmp.slice(_h(aTmp));
|
||||||
|
} else {
|
||||||
|
aTmp = aTmp.slice(0, _h(aTmp));
|
||||||
|
aDbg = aTmp; // update narrowed down list
|
||||||
|
if (aDbg.length == 1) break;
|
||||||
|
}
|
||||||
|
reapply(aALL);
|
||||||
|
myreset(aTmp.slice(0, _h(aTmp))); // reset half of the remaining prefs
|
||||||
|
}
|
||||||
|
reapply(aALL);
|
||||||
|
|
||||||
|
if (aDbg.length == 1) return alert("narrowed it down to:\n\n"+aDbg[0].name+"\n");
|
||||||
|
if (aDbg.length == aALL.length) {
|
||||||
|
const msg = "Failed to narrow it down beyond the initial "+aALL.length+" prefs. The problem is most likely caused by at least 2 prefs!\n\n" +
|
||||||
|
"Either those prefs are too far apart in the list or there are exactly 2 culprits and they just happen to be at the wrong place.\n\n" +
|
||||||
|
"In case it's the latter, the script can add a dummy pref and you can try again - Try again?";
|
||||||
|
if (confirm(msg)) return _main([...aALL, oFILLER]);
|
||||||
|
} else if (aDbg.length > 10 && confirm("Narrowed it down to "+aDbg.length+" prefs. Try narrowing it down further?")) {
|
||||||
|
return _main(aDbg.reverse());
|
||||||
|
}
|
||||||
|
|
||||||
|
alert("Narrowed it down to "+ aDbg.length.toString() +" prefs, check the console ...");
|
||||||
|
console.log('The problem is caused by 2 or more of these prefs:');
|
||||||
|
for (const oPref of aDbg) console.log(oPref.name);
|
||||||
|
}
|
||||||
|
|
||||||
|
|
||||||
|
resetAllMatchingDefault(aPREFS); // reset user-set prefs matching FFs default value
|
||||||
|
|
||||||
|
const aBAK = getMyList(aPREFS);
|
||||||
|
//console.log(aBAK.length, "user-set prefs from our list detected and their values stored.");
|
||||||
|
|
||||||
|
const sMsg = "all detected prefs reset.\n\n" +
|
||||||
|
"!! KEEP THIS PROMPT OPEN AND TEST THE SITE IN ANOTHER TAB !!\n\n" +
|
||||||
|
"IF the problem still exists, this script can't help you - click Cancel to re-apply your values and exit.\n\n" +
|
||||||
|
"Click OK if your problem is fixed.";
|
||||||
|
|
||||||
|
focus();
|
||||||
|
myreset(aBAK);
|
||||||
|
if (!confirm(sMsg)) {
|
||||||
|
reapply(aBAK);
|
||||||
|
return;
|
||||||
|
}
|
||||||
|
_main(aBAK);
|
||||||
|
|
||||||
|
})();
|
||||||
323
updater.bat
Normal file
@ -0,0 +1,323 @@
|
|||||||
|
@ECHO OFF & SETLOCAL EnableDelayedExpansion
|
||||||
|
TITLE arkenfox user.js updater
|
||||||
|
|
||||||
|
REM ## arkenfox user.js updater for Windows
|
||||||
|
REM ## author: @claustromaniac
|
||||||
|
REM ## version: 4.20
|
||||||
|
REM ## instructions: https://github.com/arkenfox/user.js/wiki/5.1-Updater-[Options]#-windows
|
||||||
|
|
||||||
|
SET v=4.19
|
||||||
|
|
||||||
|
VERIFY ON
|
||||||
|
CD /D "%~dp0"
|
||||||
|
SET _myname=%~n0
|
||||||
|
SET _myparams=%*
|
||||||
|
|
||||||
|
:parse
|
||||||
|
IF "%~1"=="" (GOTO endparse)
|
||||||
|
IF /I "%~1"=="-unattended" (SET _ua=1)
|
||||||
|
IF /I "%~1"=="-log" (SET _log=1)
|
||||||
|
IF /I "%~1"=="-logp" (SET _log=1 & SET _logp=1)
|
||||||
|
IF /I "%~1"=="-multioverrides" (SET _multi=1)
|
||||||
|
IF /I "%~1"=="-merge" (SET _merge=1)
|
||||||
|
IF /I "%~1"=="-updatebatch" (SET _updateb=1)
|
||||||
|
IF /I "%~1"=="-singlebackup" (SET _singlebackup=1)
|
||||||
|
IF /I "%~1"=="-esr" (SET _esr=1)
|
||||||
|
SHIFT
|
||||||
|
GOTO parse
|
||||||
|
:endparse
|
||||||
|
|
||||||
|
FOR /F %%i IN ('PowerShell -Command "[Enum]::GetNames([Net.SecurityProtocolType]) -contains 'Tls12'"') DO (
|
||||||
|
IF "%%i" == "False" (
|
||||||
|
CALL :message "Your PowerShell version doesn't support TLS1.2 ^!"
|
||||||
|
ECHO: Instructions to update PowerShell are on the arkenfox wiki
|
||||||
|
PAUSE
|
||||||
|
EXIT
|
||||||
|
)
|
||||||
|
)
|
||||||
|
|
||||||
|
IF DEFINED _updateb (
|
||||||
|
REM The normal flow here goes from phase 1 to phase 2 and then phase 3.
|
||||||
|
IF NOT "!_myname:~0,9!"=="[updated]" (
|
||||||
|
IF EXIST "[updated]!_myname!.bat" (
|
||||||
|
REM ## Phase 3 ##: The new script, with the original name, will:
|
||||||
|
REM * Delete the [updated]*.bat and *.bat.old scripts
|
||||||
|
REM * Begin the normal routine
|
||||||
|
FC "[updated]!_myname!.bat" "!_myname!.bat.old" >nul
|
||||||
|
IF NOT "!errorlevel!"=="0" (
|
||||||
|
CALL :message "Script updated to version !v!"
|
||||||
|
TIMEOUT 3 >nul
|
||||||
|
)
|
||||||
|
REN "[updated]!_myname!.bat" "[updated]!_myname!.bat.old"
|
||||||
|
DEL /F "!_myname!.bat.old" "[updated]!_myname!.bat.old"
|
||||||
|
GOTO begin
|
||||||
|
)
|
||||||
|
REM ## Phase 1 ##
|
||||||
|
REM * Download new batch and name it [updated]*.bat
|
||||||
|
REM * Start that script in a new CMD window
|
||||||
|
REM * Exit
|
||||||
|
CALL :message "Updating script..."
|
||||||
|
REM Uncomment the next line and comment out the PowerShell call for testing.
|
||||||
|
REM COPY /B /Y "!_myname!.bat" "[updated]!_myname!.bat" >nul
|
||||||
|
CALL :psdownload https://raw.githubusercontent.com/arkenfox/user.js/master/updater.bat "[updated]!_myname!.bat"
|
||||||
|
IF EXIST "[updated]!_myname!.bat" (
|
||||||
|
START /min CMD /C "[updated]!_myname!.bat" !_myparams!
|
||||||
|
) ELSE (
|
||||||
|
CALL :message "Failed. Make sure PowerShell is allowed internet access."
|
||||||
|
TIMEOUT 120 >nul
|
||||||
|
)
|
||||||
|
) ELSE (
|
||||||
|
IF "!_myname!"=="[updated]" (
|
||||||
|
CALL :message "The [updated] label is reserved. Rename this script and try again."
|
||||||
|
TIMEOUT 300 >nul
|
||||||
|
) ELSE (
|
||||||
|
REM ## Phase 2 ##: The [updated]*.bat script will:
|
||||||
|
REM * Rename the old script and make a copy of itself with the original name.
|
||||||
|
REM * Run that copy in a new CMD instance
|
||||||
|
REM * Exit
|
||||||
|
IF EXIST "!_myname:~9!.bat" ( REN "!_myname:~9!.bat" "!_myname:~9!.bat.old" )
|
||||||
|
COPY /B /Y "!_myname!.bat" "!_myname:~9!.bat"
|
||||||
|
START CMD /C "!_myname:~9!.bat" !_myparams!
|
||||||
|
)
|
||||||
|
)
|
||||||
|
EXIT /B
|
||||||
|
)
|
||||||
|
|
||||||
|
:begin
|
||||||
|
CLS
|
||||||
|
ECHO:
|
||||||
|
ECHO:
|
||||||
|
ECHO: ########################################
|
||||||
|
ECHO: #### user.js Updater for Windows ####
|
||||||
|
ECHO: #### by claustromaniac ####
|
||||||
|
ECHO: #### v!v! ####
|
||||||
|
ECHO: ########################################
|
||||||
|
ECHO:
|
||||||
|
SET /A "_line=0"
|
||||||
|
IF NOT EXIST user.js (
|
||||||
|
CALL :message "user.js not detected in the current directory."
|
||||||
|
) ELSE (
|
||||||
|
FOR /F "skip=1 tokens=1,* delims=:" %%G IN (user.js) DO (
|
||||||
|
SET /A "_line+=1"
|
||||||
|
IF !_line! GEQ 4 (GOTO exitloop)
|
||||||
|
IF !_line! EQU 1 (SET _name=%%H)
|
||||||
|
IF !_line! EQU 2 (SET _date=%%H)
|
||||||
|
IF !_line! EQU 3 (SET _version=%%G)
|
||||||
|
)
|
||||||
|
:exitloop
|
||||||
|
IF NOT "!_name!"=="" (
|
||||||
|
SET "_tempvar="
|
||||||
|
IF /I NOT "!_name!"=="!_name:ghacks=!" SET _tempvar=1
|
||||||
|
IF /I NOT "!_name!"=="!_name:arkenfox=!" SET _tempvar=1
|
||||||
|
IF !_tempvar! EQU 1 (
|
||||||
|
CALL :message "!_name! !_version:~2!,!_date!"
|
||||||
|
) ELSE (CALL :message "Current user.js version not recognised.")
|
||||||
|
) ELSE (CALL :message "Current user.js version not recognised.")
|
||||||
|
)
|
||||||
|
ECHO:
|
||||||
|
IF NOT DEFINED _ua (
|
||||||
|
CALL :message "This batch should be run from your Firefox profile directory."
|
||||||
|
ECHO: It will download the latest version of arkenfox user.js from github and then
|
||||||
|
CALL :message "append any of your own changes from user-overrides.js to it."
|
||||||
|
CALL :message "Visit the wiki for more detailed information."
|
||||||
|
ECHO:
|
||||||
|
TIMEOUT 1 /nobreak >nul
|
||||||
|
CHOICE /C SHE /N /M "Start [S] Help [H] Exit [E]"
|
||||||
|
CLS
|
||||||
|
IF ERRORLEVEL 3 (EXIT /B)
|
||||||
|
IF ERRORLEVEL 2 (GOTO :showhelp)
|
||||||
|
)
|
||||||
|
IF DEFINED _log (
|
||||||
|
CALL :log >>user.js-update-log.txt 2>&1
|
||||||
|
IF DEFINED _logp (START user.js-update-log.txt)
|
||||||
|
EXIT /B
|
||||||
|
:log
|
||||||
|
SET _log=2
|
||||||
|
ECHO:##################################################################
|
||||||
|
ECHO: %date%, %time%
|
||||||
|
)
|
||||||
|
IF EXIST user.js.new (DEL /F "user.js.new")
|
||||||
|
CALL :message "Retrieving latest user.js file from github repository..."
|
||||||
|
CALL :psdownload https://raw.githubusercontent.com/arkenfox/user.js/master/user.js "user.js.new"
|
||||||
|
IF EXIST user.js.new (
|
||||||
|
IF DEFINED _esr (
|
||||||
|
CALL :message "Activating ESR section..."
|
||||||
|
CALL :activate user.js.new ".x still uses all the following prefs"
|
||||||
|
)
|
||||||
|
IF DEFINED _multi (
|
||||||
|
FORFILES /P user.js-overrides /M *.js >nul 2>&1
|
||||||
|
IF NOT ERRORLEVEL 1 (
|
||||||
|
IF DEFINED _merge (
|
||||||
|
CALL :message "Merging..."
|
||||||
|
COPY /B /Y user.js-overrides\*.js user-overrides-merged.js
|
||||||
|
CALL :merge user-overrides-merged.js
|
||||||
|
COPY /B /Y user.js.new+user-overrides-merged.js user.js.new
|
||||||
|
CALL :merge user.js.new
|
||||||
|
) ELSE (
|
||||||
|
CALL :message "Appending..."
|
||||||
|
COPY /B /Y user.js.new+"user.js-overrides\*.js" user.js.new
|
||||||
|
)
|
||||||
|
) ELSE (CALL :message "No override files found.")
|
||||||
|
) ELSE (
|
||||||
|
IF EXIST "user-overrides.js" (
|
||||||
|
COPY /B /Y user.js.new+"user-overrides.js" "user.js.new"
|
||||||
|
IF DEFINED _merge (
|
||||||
|
CALL :message "Merging user-overrides.js..."
|
||||||
|
CALL :merge user.js.new
|
||||||
|
) ELSE (
|
||||||
|
CALL :message "user-overrides.js appended."
|
||||||
|
)
|
||||||
|
) ELSE (CALL :message "user-overrides.js not found.")
|
||||||
|
)
|
||||||
|
IF EXIST user.js (
|
||||||
|
FC user.js.new user.js >nul && SET "_changed=false" || SET "_changed=true"
|
||||||
|
)
|
||||||
|
IF "!_changed!"=="true" (
|
||||||
|
CALL :message "Backing up..."
|
||||||
|
IF DEFINED _singlebackup (
|
||||||
|
MOVE /Y user.js user.js.bak >nul
|
||||||
|
) ELSE (
|
||||||
|
FOR /F "delims=" %%# IN ('powershell -command get-date -format "{yyyyMMdd_HHmmss}"') DO @SET ldt=%%#
|
||||||
|
MOVE /Y user.js "user-backup-!ldt!.js" >nul
|
||||||
|
)
|
||||||
|
REN user.js.new user.js
|
||||||
|
CALL :message "Update complete."
|
||||||
|
) ELSE (
|
||||||
|
IF "!_changed!"=="false" (
|
||||||
|
DEL /F user.js.new >nul
|
||||||
|
CALL :message "Update completed without changes."
|
||||||
|
) ELSE (
|
||||||
|
REN user.js.new user.js
|
||||||
|
CALL :message "Update complete."
|
||||||
|
SET "_changed=true"
|
||||||
|
)
|
||||||
|
)
|
||||||
|
) ELSE (
|
||||||
|
CALL :message "Update failed. Make sure PowerShell is allowed internet access."
|
||||||
|
ECHO: No changes were made.
|
||||||
|
)
|
||||||
|
IF NOT DEFINED _log (
|
||||||
|
IF NOT DEFINED _ua (
|
||||||
|
IF EXIST prefsCleaner.bat (
|
||||||
|
IF "!_changed!"=="true" (
|
||||||
|
CALL :message "Would you like to run the prefsCleaner now?"
|
||||||
|
CHOICE /C YN /N /M "(Y/N) "
|
||||||
|
IF "1"=="!errorlevel!" ( START "" cmd.exe /C "prefsCleaner.bat" )
|
||||||
|
) ELSE (PAUSE)
|
||||||
|
) ELSE (PAUSE)
|
||||||
|
)
|
||||||
|
)
|
||||||
|
EXIT /B
|
||||||
|
|
||||||
|
::::::::::::::: Message :::::::::::::::
|
||||||
|
:message
|
||||||
|
SETLOCAL DisableDelayedExpansion
|
||||||
|
IF NOT "2"=="%_log%" (ECHO:)
|
||||||
|
ECHO: %~1
|
||||||
|
IF NOT "2"=="%_log%" (ECHO:)
|
||||||
|
ENDLOCAL
|
||||||
|
GOTO :EOF
|
||||||
|
|
||||||
|
::::::::::::::: Download :::::::::::::::
|
||||||
|
:psdownload
|
||||||
|
(
|
||||||
|
PowerShell -Command "[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; (New-Object Net.WebClient).DownloadFile('%~1', '%~2')"
|
||||||
|
) >nul 2>&1
|
||||||
|
GOTO :EOF
|
||||||
|
|
||||||
|
::::::::::::::: Activate Section :::::::::::::::
|
||||||
|
:activate
|
||||||
|
:: arg1 = file
|
||||||
|
:: arg2 = line substring
|
||||||
|
SETLOCAL DisableDelayedExpansion
|
||||||
|
(
|
||||||
|
FOR /F "tokens=1,* delims=:" %%G IN ('FINDSTR /N "^" "%~1"') DO (
|
||||||
|
SET "_temp=%%H"
|
||||||
|
SETLOCAL EnableDelayedExpansion
|
||||||
|
IF "!_temp:%~2=!"=="!_temp!" (
|
||||||
|
ENDLOCAL & ECHO:%%H
|
||||||
|
) ELSE (
|
||||||
|
ECHO://!_temp:~2!
|
||||||
|
ENDLOCAL
|
||||||
|
)
|
||||||
|
)
|
||||||
|
)>updatertempfile
|
||||||
|
MOVE /Y updatertempfile "%~1" >nul
|
||||||
|
ENDLOCAL
|
||||||
|
GOTO :EOF
|
||||||
|
|
||||||
|
::::::::::::::: Merge :::::::::::::::
|
||||||
|
:merge
|
||||||
|
SETLOCAL DisableDelayedExpansion
|
||||||
|
FOR /F tokens^=2^,^*^ delims^=^'^" %%G IN ('FINDSTR /R /C:"^user_pref[ ]*\([ ]*[\"'].*[\"'][ ]*,.*\)[ ]*;" "%~1"') DO (SET "[%%G]=%%H")
|
||||||
|
FOR /F tokens^=2^,^*^ delims^=^' %%G IN ('FINDSTR /R /C:"^//// --- comment-out --- '[^'][^']*'.*" "%~1"') DO (SET "__unset__%%G=1")
|
||||||
|
(
|
||||||
|
FOR /F "tokens=1,* delims=:" %%I IN ('FINDSTR /N "^" "%~1"') DO (
|
||||||
|
SET "_temp=%%J"
|
||||||
|
SETLOCAL EnableDelayedExpansion
|
||||||
|
IF NOT "!_temp:~0,9!"=="user_pref" (
|
||||||
|
ENDLOCAL & ECHO:%%J
|
||||||
|
) ELSE (
|
||||||
|
IF "!_temp:;=!"=="!_temp!" (
|
||||||
|
ENDLOCAL & ECHO:%%J
|
||||||
|
) ELSE (
|
||||||
|
ENDLOCAL
|
||||||
|
FOR /F tokens^=2^ delims^=^'^" %%K IN ("%%J") DO (
|
||||||
|
IF NOT "_user.js.parrot"=="%%K" (
|
||||||
|
IF DEFINED __unset__%%K (
|
||||||
|
ECHO://%%J
|
||||||
|
) ELSE (
|
||||||
|
IF DEFINED [%%K] (
|
||||||
|
SETLOCAL EnableDelayedExpansion
|
||||||
|
FOR /F "delims=" %%L IN ("![%%K]!") DO (
|
||||||
|
ENDLOCAL & ECHO:user_pref("%%K"%%L
|
||||||
|
SET "[%%K]="
|
||||||
|
)
|
||||||
|
)
|
||||||
|
)
|
||||||
|
) ELSE (ECHO:%%J)
|
||||||
|
)
|
||||||
|
)
|
||||||
|
)
|
||||||
|
)
|
||||||
|
)>updatertempfile
|
||||||
|
MOVE /Y updatertempfile "%~1" >nul
|
||||||
|
ENDLOCAL
|
||||||
|
GOTO :EOF
|
||||||
|
|
||||||
|
::::::::::::::: Help :::::::::::::::
|
||||||
|
:showhelp
|
||||||
|
MODE 80,54
|
||||||
|
CLS
|
||||||
|
CALL :message "Available arguments (case-insensitive):"
|
||||||
|
CALL :message " -esr"
|
||||||
|
ECHO: Activate ESR related preferences
|
||||||
|
CALL :message " -log"
|
||||||
|
ECHO: Write the console output to a logfile (user.js-update-log.txt)
|
||||||
|
CALL :message " -logP"
|
||||||
|
ECHO: Like -log, but also open the logfile after updating.
|
||||||
|
CALL :message " -merge"
|
||||||
|
ECHO: Merge overrides instead of appending them. Single-line comments and
|
||||||
|
ECHO: _user.js.parrot lines are appended normally. Overrides for inactive
|
||||||
|
ECHO: user.js prefs will be appended. When -Merge and -MultiOverrides are used
|
||||||
|
ECHO: together, a user-overrides-merged.js file is also generated in the root
|
||||||
|
ECHO: directory for quick reference. It contains only the merged data from
|
||||||
|
ECHO: override files and can be safely discarded after updating, or used as the
|
||||||
|
ECHO: new user-overrides.js. When there are conflicting records for the same
|
||||||
|
ECHO: pref, the value of the last one declared will be used. Visit the wiki
|
||||||
|
ECHO: for usage examples and more detailed information.
|
||||||
|
CALL :message " -multiOverrides"
|
||||||
|
ECHO: Use any and all .js files in a user.js-overrides sub-folder as overrides
|
||||||
|
ECHO: instead of the default user-overrides.js file. Files are appended in
|
||||||
|
ECHO: alphabetical order.
|
||||||
|
CALL :message " -unattended"
|
||||||
|
ECHO: Run without user input.
|
||||||
|
CALL :message " -singleBackup"
|
||||||
|
ECHO: Use a single backup file and overwrite it on new updates, instead of
|
||||||
|
ECHO: cumulative backups. This was the default behaviour before v4.3.
|
||||||
|
CALL :message " -updateBatch"
|
||||||
|
ECHO: Update the script itself on execution, before the normal routine.
|
||||||
|
CALL :message ""
|
||||||
|
PAUSE
|
||||||
|
MODE 80,25
|
||||||
|
GOTO :begin
|
||||||
407
updater.sh
Executable file
@ -0,0 +1,407 @@
|
|||||||
|
#!/usr/bin/env bash
|
||||||
|
|
||||||
|
## arkenfox user.js updater for macOS and Linux
|
||||||
|
|
||||||
|
## version: 4.0
|
||||||
|
## Author: Pat Johnson (@overdodactyl)
|
||||||
|
## Additional contributors: @earthlng, @ema-pe, @claustromaniac, @infinitewarp
|
||||||
|
|
||||||
|
## DON'T GO HIGHER THAN VERSION x.9 !! ( because of ASCII comparison in update_updater() )
|
||||||
|
|
||||||
|
# Check if running as root
|
||||||
|
if [ "${EUID:-"$(id -u)"}" -eq 0 ]; then
|
||||||
|
printf "You shouldn't run this with elevated privileges (such as with doas/sudo).\n"
|
||||||
|
exit 1
|
||||||
|
fi
|
||||||
|
|
||||||
|
readonly CURRDIR=$(pwd)
|
||||||
|
|
||||||
|
SCRIPT_FILE=$(readlink -f "${BASH_SOURCE[0]}" 2>/dev/null || greadlink -f "${BASH_SOURCE[0]}" 2>/dev/null)
|
||||||
|
[ -z "$SCRIPT_FILE" ] && SCRIPT_FILE=${BASH_SOURCE[0]}
|
||||||
|
readonly SCRIPT_DIR=$(dirname "${SCRIPT_FILE}")
|
||||||
|
|
||||||
|
|
||||||
|
#########################
|
||||||
|
# Base variables #
|
||||||
|
#########################
|
||||||
|
|
||||||
|
# Colors used for printing
|
||||||
|
RED='\033[0;31m'
|
||||||
|
BLUE='\033[0;34m'
|
||||||
|
BBLUE='\033[1;34m'
|
||||||
|
GREEN='\033[0;32m'
|
||||||
|
ORANGE='\033[0;33m'
|
||||||
|
CYAN='\033[0;36m'
|
||||||
|
NC='\033[0m' # No Color
|
||||||
|
|
||||||
|
# Argument defaults
|
||||||
|
UPDATE='check'
|
||||||
|
CONFIRM='yes'
|
||||||
|
OVERRIDE='user-overrides.js'
|
||||||
|
BACKUP='multiple'
|
||||||
|
COMPARE=false
|
||||||
|
SKIPOVERRIDE=false
|
||||||
|
VIEW=false
|
||||||
|
PROFILE_PATH=false
|
||||||
|
ESR=false
|
||||||
|
|
||||||
|
# Download method priority: curl -> wget
|
||||||
|
DOWNLOAD_METHOD=''
|
||||||
|
if command -v curl >/dev/null; then
|
||||||
|
DOWNLOAD_METHOD='curl --max-redirs 3 -so'
|
||||||
|
elif command -v wget >/dev/null; then
|
||||||
|
DOWNLOAD_METHOD='wget --max-redirect 3 --quiet -O'
|
||||||
|
else
|
||||||
|
echo -e "${RED}This script requires curl or wget.\nProcess aborted${NC}"
|
||||||
|
exit 1
|
||||||
|
fi
|
||||||
|
|
||||||
|
|
||||||
|
show_banner() {
|
||||||
|
echo -e "${BBLUE}
|
||||||
|
############################################################################
|
||||||
|
#### ####
|
||||||
|
#### arkenfox user.js ####
|
||||||
|
#### Hardening the Privacy and Security Settings of Firefox ####
|
||||||
|
#### Maintained by @Thorin-Oakenpants and @earthlng ####
|
||||||
|
#### Updater for macOS and Linux by @overdodactyl ####
|
||||||
|
#### ####
|
||||||
|
############################################################################"
|
||||||
|
echo -e "${NC}\n"
|
||||||
|
echo -e "Documentation for this script is available here: ${CYAN}https://github.com/arkenfox/user.js/wiki/5.1-Updater-[Options]#-maclinux${NC}\n"
|
||||||
|
}
|
||||||
|
|
||||||
|
#########################
|
||||||
|
# Arguments #
|
||||||
|
#########################
|
||||||
|
|
||||||
|
usage() {
|
||||||
|
echo
|
||||||
|
echo -e "${BLUE}Usage: $0 [-bcdehlnrsuv] [-p PROFILE] [-o OVERRIDE]${NC}" 1>&2 # Echo usage string to standard error
|
||||||
|
echo -e "
|
||||||
|
Optional Arguments:
|
||||||
|
-h Show this help message and exit.
|
||||||
|
-p PROFILE Path to your Firefox profile (if different than the dir of this script)
|
||||||
|
IMPORTANT: If the path contains spaces, wrap the entire argument in quotes.
|
||||||
|
-l Choose your Firefox profile from a list
|
||||||
|
-u Update updater.sh and execute silently. Do not seek confirmation.
|
||||||
|
-d Do not look for updates to updater.sh.
|
||||||
|
-s Silently update user.js. Do not seek confirmation.
|
||||||
|
-b Only keep one backup of each file.
|
||||||
|
-c Create a diff file comparing old and new user.js within userjs_diffs.
|
||||||
|
-o OVERRIDE Filename or path to overrides file (if different than user-overrides.js).
|
||||||
|
If used with -p, paths should be relative to PROFILE or absolute paths
|
||||||
|
If given a directory, all files inside will be appended recursively.
|
||||||
|
You can pass multiple files or directories by passing a comma separated list.
|
||||||
|
Note: If a directory is given, only files inside ending in the extension .js are appended
|
||||||
|
IMPORTANT: Do not add spaces between files/paths. Ex: -o file1.js,file2.js,dir1
|
||||||
|
IMPORTANT: If any file/path contains spaces, wrap the entire argument in quotes.
|
||||||
|
Ex: -o \"override folder\"
|
||||||
|
-n Do not append any overrides, even if user-overrides.js exists.
|
||||||
|
-v Open the resulting user.js file.
|
||||||
|
-r Only download user.js to a temporary file and open it.
|
||||||
|
-e Activate ESR related preferences."
|
||||||
|
echo
|
||||||
|
exit 1
|
||||||
|
}
|
||||||
|
|
||||||
|
#########################
|
||||||
|
# File Handling #
|
||||||
|
#########################
|
||||||
|
|
||||||
|
download_file() { # expects URL as argument ($1)
|
||||||
|
declare -r tf=$(mktemp)
|
||||||
|
|
||||||
|
$DOWNLOAD_METHOD "${tf}" "$1" &>/dev/null && echo "$tf" || echo '' # return the temp-filename or empty string on error
|
||||||
|
}
|
||||||
|
|
||||||
|
open_file() { # expects one argument: file_path
|
||||||
|
if [ "$(uname)" == 'Darwin' ]; then
|
||||||
|
open "$1"
|
||||||
|
elif [ "$(uname -s | cut -c -5)" == "Linux" ]; then
|
||||||
|
xdg-open "$1"
|
||||||
|
else
|
||||||
|
echo -e "${RED}Error: Sorry, opening files is not supported for your OS.${NC}"
|
||||||
|
fi
|
||||||
|
}
|
||||||
|
|
||||||
|
readIniFile() { # expects one argument: absolute path of profiles.ini
|
||||||
|
declare -r inifile="$1"
|
||||||
|
|
||||||
|
# tempIni will contain: [ProfileX], Name=, IsRelative= and Path= (and Default= if present) of the only (if) or the selected (else) profile
|
||||||
|
if [ "$(grep -c '^\[Profile' "${inifile}")" -eq "1" ]; then ### only 1 profile found
|
||||||
|
tempIni="$(grep '^\[Profile' -A 4 "${inifile}")"
|
||||||
|
else
|
||||||
|
echo -e "Profiles found:\n––––––––––––––––––––––––––––––"
|
||||||
|
## cmd-substitution to strip trailing newlines and in quotes to keep internal ones:
|
||||||
|
echo "$(grep --color=never -E 'Default=[^1]|\[Profile[0-9]*\]|Name=|Path=|^$' "${inifile}")"
|
||||||
|
echo '––––––––––––––––––––––––––––––'
|
||||||
|
read -p 'Select the profile number ( 0 for Profile0, 1 for Profile1, etc ) : ' -r
|
||||||
|
echo -e "\n"
|
||||||
|
if [[ $REPLY =~ ^(0|[1-9][0-9]*)$ ]]; then
|
||||||
|
tempIni="$(grep "^\[Profile${REPLY}" -A 4 "${inifile}")" || {
|
||||||
|
echo -e "${RED}Profile${REPLY} does not exist!${NC}" && exit 1
|
||||||
|
}
|
||||||
|
else
|
||||||
|
echo -e "${RED}Invalid selection!${NC}" && exit 1
|
||||||
|
fi
|
||||||
|
fi
|
||||||
|
|
||||||
|
# extracting 0 or 1 from the "IsRelative=" line
|
||||||
|
declare -r pathisrel=$(sed -n 's/^IsRelative=\([01]\)$/\1/p' <<< "${tempIni}")
|
||||||
|
|
||||||
|
# extracting only the path itself, excluding "Path="
|
||||||
|
PROFILE_PATH=$(sed -n 's/^Path=\(.*\)$/\1/p' <<< "${tempIni}")
|
||||||
|
# update global variable if path is relative
|
||||||
|
[[ ${pathisrel} == "1" ]] && PROFILE_PATH="$(dirname "${inifile}")/${PROFILE_PATH}"
|
||||||
|
}
|
||||||
|
|
||||||
|
getProfilePath() {
|
||||||
|
declare -r f1=~/Library/Application\ Support/Firefox/profiles.ini
|
||||||
|
declare -r f2=~/.mozilla/firefox/profiles.ini
|
||||||
|
|
||||||
|
if [ "$PROFILE_PATH" = false ]; then
|
||||||
|
PROFILE_PATH="$SCRIPT_DIR"
|
||||||
|
elif [ "$PROFILE_PATH" = 'list' ]; then
|
||||||
|
if [[ -f "$f1" ]]; then
|
||||||
|
readIniFile "$f1" # updates PROFILE_PATH or exits on error
|
||||||
|
elif [[ -f "$f2" ]]; then
|
||||||
|
readIniFile "$f2"
|
||||||
|
else
|
||||||
|
echo -e "${RED}Error: Sorry, -l is not supported for your OS${NC}"
|
||||||
|
exit 1
|
||||||
|
fi
|
||||||
|
#else
|
||||||
|
# PROFILE_PATH already set by user with -p
|
||||||
|
fi
|
||||||
|
}
|
||||||
|
|
||||||
|
#########################
|
||||||
|
# Update updater.sh #
|
||||||
|
#########################
|
||||||
|
|
||||||
|
# Returns the version number of a updater.sh file
|
||||||
|
get_updater_version() {
|
||||||
|
echo "$(sed -n '5 s/.*[[:blank:]]\([[:digit:]]*\.[[:digit:]]*\)/\1/p' "$1")"
|
||||||
|
}
|
||||||
|
|
||||||
|
# Update updater.sh
|
||||||
|
# Default: Check for update, if available, ask user if they want to execute it
|
||||||
|
# Args:
|
||||||
|
# -d: New version will not be looked for and update will not occur
|
||||||
|
# -u: Check for update, if available, execute without asking
|
||||||
|
update_updater() {
|
||||||
|
[ "$UPDATE" = 'no' ] && return 0 # User signified not to check for updates
|
||||||
|
|
||||||
|
declare -r tmpfile="$(download_file 'https://raw.githubusercontent.com/arkenfox/user.js/master/updater.sh')"
|
||||||
|
[ -z "${tmpfile}" ] && echo -e "${RED}Error! Could not download updater.sh${NC}" && return 1 # check if download failed
|
||||||
|
|
||||||
|
if [[ $(get_updater_version "$SCRIPT_FILE") < $(get_updater_version "${tmpfile}") ]]; then
|
||||||
|
if [ "$UPDATE" = 'check' ]; then
|
||||||
|
echo -e "There is a newer version of updater.sh available. ${RED}Update and execute Y/N?${NC}"
|
||||||
|
read -p "" -n 1 -r
|
||||||
|
echo -e "\n\n"
|
||||||
|
[[ $REPLY =~ ^[Yy]$ ]] || return 0 # Update available, but user chooses not to update
|
||||||
|
fi
|
||||||
|
else
|
||||||
|
return 0 # No update available
|
||||||
|
fi
|
||||||
|
mv "${tmpfile}" "$SCRIPT_FILE"
|
||||||
|
chmod u+x "$SCRIPT_FILE"
|
||||||
|
"$SCRIPT_FILE" "$@" -d
|
||||||
|
exit 0
|
||||||
|
}
|
||||||
|
|
||||||
|
#########################
|
||||||
|
# Update user.js #
|
||||||
|
#########################
|
||||||
|
|
||||||
|
# Returns version number of a user.js file
|
||||||
|
get_userjs_version() {
|
||||||
|
[ -e "$1" ] && echo "$(sed -n '4p' "$1")" || echo "Not detected."
|
||||||
|
}
|
||||||
|
|
||||||
|
add_override() {
|
||||||
|
input=$1
|
||||||
|
if [ -f "$input" ]; then
|
||||||
|
echo "" >> user.js
|
||||||
|
cat "$input" >> user.js
|
||||||
|
echo -e "Status: ${GREEN}Override file appended:${NC} ${input}"
|
||||||
|
elif [ -d "$input" ]; then
|
||||||
|
SAVEIFS=$IFS
|
||||||
|
IFS=$'\n\b' # Set IFS
|
||||||
|
FILES="${input}"/*.js
|
||||||
|
for f in $FILES
|
||||||
|
do
|
||||||
|
add_override "$f"
|
||||||
|
done
|
||||||
|
IFS=$SAVEIFS # restore $IFS
|
||||||
|
else
|
||||||
|
echo -e "${ORANGE}Warning: Could not find override file:${NC} ${input}"
|
||||||
|
fi
|
||||||
|
}
|
||||||
|
|
||||||
|
remove_comments() { # expects 2 arguments: from-file and to-file
|
||||||
|
sed -e '/^\/\*.*\*\/[[:space:]]*$/d' -e '/^\/\*/,/\*\//d' -e 's|^[[:space:]]*//.*$||' -e '/^[[:space:]]*$/d' -e 's|);[[:space:]]*//.*|);|' "$1" > "$2"
|
||||||
|
}
|
||||||
|
|
||||||
|
# Applies latest version of user.js and any custom overrides
|
||||||
|
update_userjs() {
|
||||||
|
declare -r newfile="$(download_file 'https://raw.githubusercontent.com/arkenfox/user.js/master/user.js')"
|
||||||
|
[ -z "${newfile}" ] && echo -e "${RED}Error! Could not download user.js${NC}" && return 1 # check if download failed
|
||||||
|
|
||||||
|
echo -e "Please observe the following information:
|
||||||
|
Firefox profile: ${ORANGE}$(pwd)${NC}
|
||||||
|
Available online: ${ORANGE}$(get_userjs_version "$newfile")${NC}
|
||||||
|
Currently using: ${ORANGE}$(get_userjs_version user.js)${NC}\n\n"
|
||||||
|
|
||||||
|
if [ "$CONFIRM" = 'yes' ]; then
|
||||||
|
echo -e "This script will update to the latest user.js file and append any custom configurations from user-overrides.js. ${RED}Continue Y/N? ${NC}"
|
||||||
|
read -p "" -n 1 -r
|
||||||
|
echo -e "\n"
|
||||||
|
if ! [[ $REPLY =~ ^[Yy]$ ]]; then
|
||||||
|
echo -e "${RED}Process aborted${NC}"
|
||||||
|
rm "$newfile"
|
||||||
|
return 1
|
||||||
|
fi
|
||||||
|
fi
|
||||||
|
|
||||||
|
# Copy a version of user.js to diffs folder for later comparison
|
||||||
|
if [ "$COMPARE" = true ]; then
|
||||||
|
mkdir -p userjs_diffs
|
||||||
|
cp user.js userjs_diffs/past_user.js &>/dev/null
|
||||||
|
fi
|
||||||
|
|
||||||
|
# backup user.js
|
||||||
|
mkdir -p userjs_backups
|
||||||
|
local bakname="userjs_backups/user.js.backup.$(date +"%Y-%m-%d_%H%M")"
|
||||||
|
[ "$BACKUP" = 'single' ] && bakname='userjs_backups/user.js.backup'
|
||||||
|
cp user.js "$bakname" &>/dev/null
|
||||||
|
|
||||||
|
mv "${newfile}" user.js
|
||||||
|
echo -e "Status: ${GREEN}user.js has been backed up and replaced with the latest version!${NC}"
|
||||||
|
|
||||||
|
if [ "$ESR" = true ]; then
|
||||||
|
sed -e 's/\/\* \(ESR[0-9]\{2,\}\.x still uses all.*\)/\/\/ \1/' user.js > user.js.tmp && mv user.js.tmp user.js
|
||||||
|
echo -e "Status: ${GREEN}ESR related preferences have been activated!${NC}"
|
||||||
|
fi
|
||||||
|
|
||||||
|
# apply overrides
|
||||||
|
if [ "$SKIPOVERRIDE" = false ]; then
|
||||||
|
while IFS=',' read -ra FILES; do
|
||||||
|
for FILE in "${FILES[@]}"; do
|
||||||
|
add_override "$FILE"
|
||||||
|
done
|
||||||
|
done <<< "$OVERRIDE"
|
||||||
|
fi
|
||||||
|
|
||||||
|
# create diff
|
||||||
|
if [ "$COMPARE" = true ]; then
|
||||||
|
pastuserjs='userjs_diffs/past_user.js'
|
||||||
|
past_nocomments='userjs_diffs/past_userjs.txt'
|
||||||
|
current_nocomments='userjs_diffs/current_userjs.txt'
|
||||||
|
|
||||||
|
remove_comments "$pastuserjs" "$past_nocomments"
|
||||||
|
remove_comments user.js "$current_nocomments"
|
||||||
|
|
||||||
|
diffname="userjs_diffs/diff_$(date +"%Y-%m-%d_%H%M").txt"
|
||||||
|
diff=$(diff -w -B -U 0 "$past_nocomments" "$current_nocomments")
|
||||||
|
if [ -n "$diff" ]; then
|
||||||
|
echo "$diff" > "$diffname"
|
||||||
|
echo -e "Status: ${GREEN}A diff file was created:${NC} ${PWD}/${diffname}"
|
||||||
|
else
|
||||||
|
echo -e "Warning: ${ORANGE}Your new user.js file appears to be identical. No diff file was created.${NC}"
|
||||||
|
[ "$BACKUP" = 'multiple' ] && rm "$bakname" &>/dev/null
|
||||||
|
fi
|
||||||
|
rm "$past_nocomments" "$current_nocomments" "$pastuserjs" &>/dev/null
|
||||||
|
fi
|
||||||
|
|
||||||
|
[ "$VIEW" = true ] && open_file "${PWD}/user.js"
|
||||||
|
}
|
||||||
|
|
||||||
|
#########################
|
||||||
|
# Execute #
|
||||||
|
#########################
|
||||||
|
|
||||||
|
if [ $# != 0 ]; then
|
||||||
|
# Display usage if first argument is -help or --help
|
||||||
|
if [ "$1" = '--help' ] || [ "$1" = '-help' ]; then
|
||||||
|
usage
|
||||||
|
else
|
||||||
|
while getopts ":hp:ludsno:bcvre" opt; do
|
||||||
|
case $opt in
|
||||||
|
h)
|
||||||
|
usage
|
||||||
|
;;
|
||||||
|
p)
|
||||||
|
PROFILE_PATH=${OPTARG}
|
||||||
|
;;
|
||||||
|
l)
|
||||||
|
PROFILE_PATH='list'
|
||||||
|
;;
|
||||||
|
u)
|
||||||
|
UPDATE='yes'
|
||||||
|
;;
|
||||||
|
d)
|
||||||
|
UPDATE='no'
|
||||||
|
;;
|
||||||
|
s)
|
||||||
|
CONFIRM='no'
|
||||||
|
;;
|
||||||
|
n)
|
||||||
|
SKIPOVERRIDE=true
|
||||||
|
;;
|
||||||
|
o)
|
||||||
|
OVERRIDE=${OPTARG}
|
||||||
|
;;
|
||||||
|
b)
|
||||||
|
BACKUP='single'
|
||||||
|
;;
|
||||||
|
c)
|
||||||
|
COMPARE=true
|
||||||
|
;;
|
||||||
|
v)
|
||||||
|
VIEW=true
|
||||||
|
;;
|
||||||
|
e)
|
||||||
|
ESR=true
|
||||||
|
;;
|
||||||
|
r)
|
||||||
|
tfile="$(download_file 'https://raw.githubusercontent.com/arkenfox/user.js/master/user.js')"
|
||||||
|
[ -z "${tfile}" ] && echo -e "${RED}Error! Could not download user.js${NC}" && exit 1 # check if download failed
|
||||||
|
mv "$tfile" "${tfile}.js"
|
||||||
|
echo -e "${ORANGE}Warning: user.js was saved to temporary file ${tfile}.js${NC}"
|
||||||
|
open_file "${tfile}.js"
|
||||||
|
exit 0
|
||||||
|
;;
|
||||||
|
\?)
|
||||||
|
echo -e "${RED}\n Error! Invalid option: -$OPTARG${NC}" >&2
|
||||||
|
usage
|
||||||
|
;;
|
||||||
|
:)
|
||||||
|
echo -e "${RED}Error! Option -$OPTARG requires an argument.${NC}" >&2
|
||||||
|
exit 2
|
||||||
|
;;
|
||||||
|
esac
|
||||||
|
done
|
||||||
|
fi
|
||||||
|
fi
|
||||||
|
|
||||||
|
show_banner
|
||||||
|
update_updater "$@"
|
||||||
|
|
||||||
|
getProfilePath # updates PROFILE_PATH or exits on error
|
||||||
|
cd "$PROFILE_PATH" || exit 1
|
||||||
|
|
||||||
|
# Check if any files have the owner as root/wheel.
|
||||||
|
if [ -n "$(find ./ -user 0)" ]; then
|
||||||
|
printf 'It looks like this script was previously run with elevated privileges,
|
||||||
|
you will need to change ownership of the following files to your user:\n'
|
||||||
|
find . -user 0
|
||||||
|
cd "$CURRDIR"
|
||||||
|
exit 1
|
||||||
|
fi
|
||||||
|
|
||||||
|
update_userjs
|
||||||
|
|
||||||
|
cd "$CURRDIR"
|
||||||
1
wikipiki/License-MIT-yellow.svg
Normal file
@ -0,0 +1 @@
|
|||||||
|
<svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="78" height="20"><linearGradient id="b" x2="0" y2="100%"><stop offset="0" stop-color="#bbb" stop-opacity=".1"/><stop offset="1" stop-opacity=".1"/></linearGradient><clipPath id="a"><rect width="78" height="20" rx="3" fill="#fff"/></clipPath><g clip-path="url(#a)"><path fill="#555" d="M0 0h47v20H0z"/><path fill="#dfb317" d="M47 0h31v20H47z"/><path fill="url(#b)" d="M0 0h78v20H0z"/></g><g fill="#fff" text-anchor="middle" font-family="DejaVu Sans,Verdana,Geneva,sans-serif" font-size="110"> <text x="245" y="150" fill="#010101" fill-opacity=".3" transform="scale(.1)" textLength="370">license</text><text x="245" y="140" transform="scale(.1)" textLength="370">license</text><text x="615" y="150" fill="#010101" fill-opacity=".3" transform="scale(.1)" textLength="210">MIT</text><text x="615" y="140" transform="scale(.1)" textLength="210">MIT</text></g> </svg>
|
||||||
|
After (image error) Size: 950 B |
|
Before 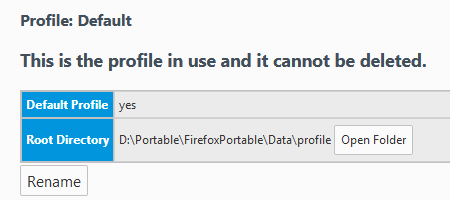
(image error) Size: 5.5 KiB |
|
Before 
(image error) Size: 3.3 KiB |
|
Before 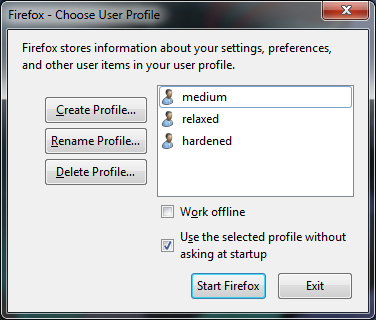
(image error) Size: 32 KiB |
|
Before 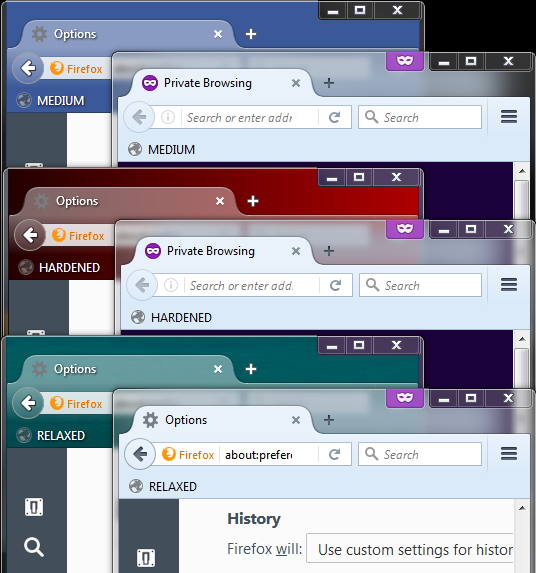
(image error) Size: 104 KiB |
|
Before 
(image error) Size: 28 KiB |
|
Before 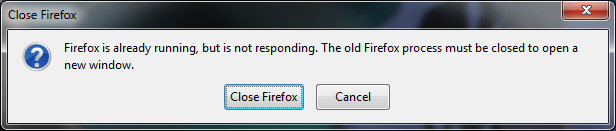
(image error) Size: 28 KiB |
BIN
wikipiki/icon-librewolf.png
Normal file
|
After (image error) Size: 1.2 KiB |
BIN
wikipiki/icon-mull.png
Normal file
|
After (image error) Size: 1.5 KiB |
BIN
wikipiki/icon-mullvadbrowser.png
Normal file
|
After (image error) Size: 1.2 KiB |
BIN
wikipiki/icon-torbrowser.png
Normal file
|
After (image error) Size: 2.0 KiB |
|
Before 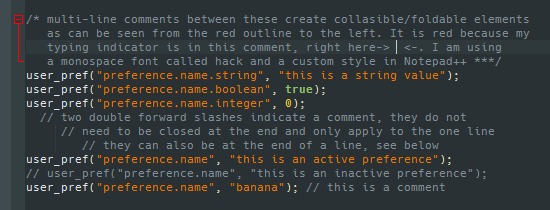
(image error) Size: 19 KiB |
|
Before 
(image error) Size: 11 KiB |
|
Before 
(image error) Size: 18 KiB |
BIN
wikipiki/parseError.png
Normal file
|
After 
(image error) Size: 3.4 KiB |
|
Before 
(image error) Size: 32 KiB |
|
Before 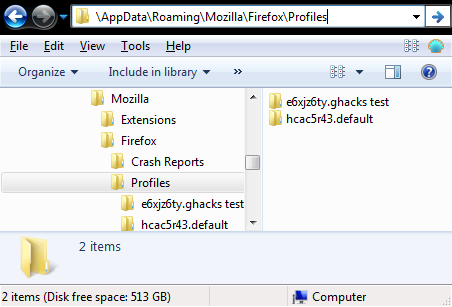
(image error) Size: 26 KiB |
BIN
wikipiki/rfpCanvas.png
Normal file
|
After 
(image error) Size: 5.4 KiB |
BIN
wikipiki/rfpCanvasException.png
Normal file
|
After 
(image error) Size: 7.6 KiB |
BIN
wikipiki/uboCustom.png
Normal file
|
After 
(image error) Size: 12 KiB |