Countering AMSI Detection
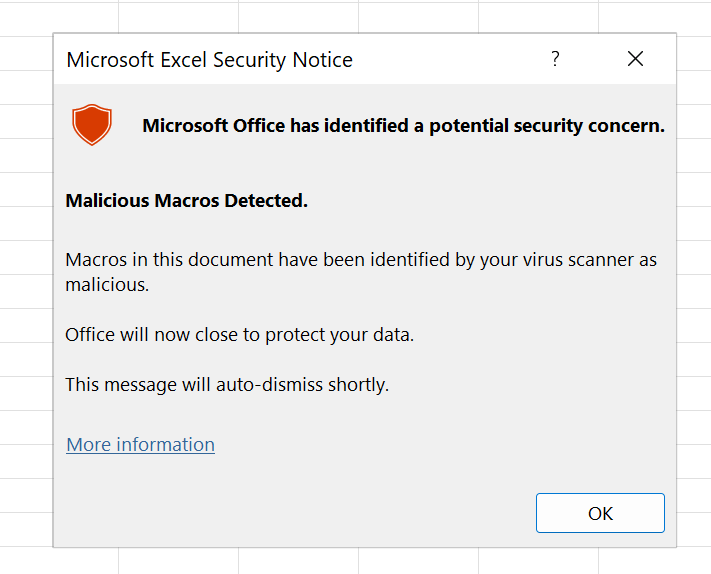
This page explains how to troubleshoot AMSI detections on Office documents. This is the typical error message indicating AMSI killed our maldoc:
The script provided in this directory, again, uses splendid work of Matt Graeber, @mattifestation, namely his AMSITools.ps1 script, that pulls AMSI events from Windows' event-log.
Pulling AMSI Events
We can pull AMSI events to review more closely what happened thanks to Matt's AMSITools.ps1.
Follow these steps:
-
Disable your Anti-Virus. In Defender, that includes turning off Real-Time Detection option.
-
Open up Powershell as Administrator and browse to this script's directory.
-
Load up
Get-AMSIScanResult.ps1script:
PS D:\AMSITools> . .\Get-AMSIScanResult.ps1
- And then - to inspect Office document - simply launch the following:
PS D:\AMSITools> Get-AMSIScanResult -Interactive
- You will be prompted with following message:
Trigger AMSI detections now and then press any key to pull AMSI events...
-
Now re-enable your Anti-Virus, to make sure AMSI provider will be active and Maldoc will get remediated.
-
Open up your faulty Maldoc document to ensure AMSI triggers and event gets generated
-
After seeing AMSI error dialog, close up Office application and get back to Powershell console.
-
Now hit Enter in the console and review output or follow instructions.
Example Event
Example event look like following:
ProcessId : 30828
ThreadId : 14248
TimeCreated : 02/09/2022 16:54:54
Session : 0
ScanStatus : 1
ScanResult : AMSI_RESULT_DETECTED
AppName : OFFICE_VBA
ContentName : D:\rmf\output-files\evil2.xlsm
ContentSize : 680
OriginalSize : 680
Content : IXMLDOMDocument2.createelement("obf_someInternalName");
IXMLDOMElement.nodetypedvalue();
IXMLDOMDocument2.createelement("obf_someInternalName");
IXMLDOMElement.nodetypedvalue();
IXMLDOMDocument2.createelement("obf_someInternalName");
IXMLDOMElement.nodetypedvalue();
IWshShell3.run("false", "0", "%WINDIR%\System32\conhost.exe "calc" """);
Hash : 6C58AE0705D2CE87ED36E78E6C366118AA407776D898864F92FF5ADC50294268
ContentFiltered : False
The very last line of Content entry tells us, which was the last VBA line of code that generated AMSI event.
Credits
All credits go to Matt - this directory contains HIS script AMSITools.ps1, mirrored for preserverance purposes.